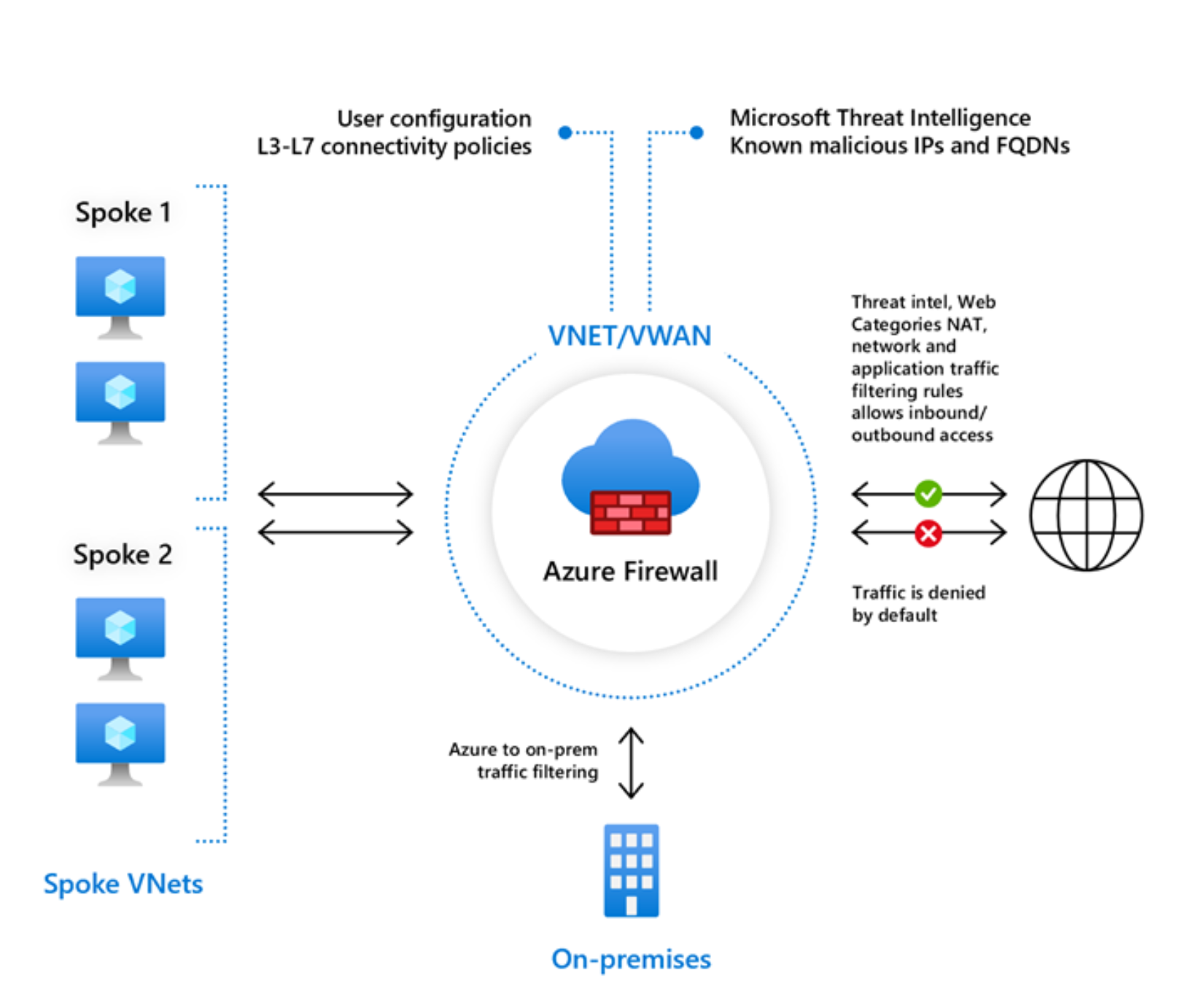
Tufin has a strong relationship with many cloud providers, including Microsoft Azure, and one powerful element of the Azure ecosystem is Azure Firewall, a managed, cloud-based network security service that protects Azure Virtual Network resources.
Azure Firewall delivers the functionality of a fully stateful firewall-as-a-service that benefits from high availability and unrestricted cloud scalability. You can use Azure Firewall in a hub virtual network to route and filter traffic between multiple spoke virtual networks.
Tufin can help you gain visibility into the fundamentals of your Azure Firewall and automate firewall rule changes. Tufin provides insights into risks, redundancy, and compliance violations. Proper management of firewall rule sets and configurations can help prevent vulnerabilities and optimize network traffic, especially when combined with the end-to-end automation of firewall changes Tufin provides.
How to Manage Azure Firewall Rules
As you configure Azure Firewall, note that it supports rules and rule collections, which are sets of rules that share the same order and priority, according to Microsoft. Further, Azure Firewall rule collections are run in order of their priority.
Rule collection groups with lower numbers are prioritized more than those with higher numbers, on a scale from 100 to 65,000. Microsoft advises admins to space rule collection priority numbers in 100-number increments (100, 200, 300, and so on) to ensure space to add more rule collections if needed.
According to Microsoft, Destination Network Address Translation (DNAT) rule collections filter and translate inbound internet traffic to subnets, higher-priority network rule collections.
Per Microsoft, there are three rule types in terms of rule collections for Azure Firewall:
- Network rules configure rules that contain source IP addresses, protocols, destination ports, and destination addresses.
- Application rules configure fully qualified domain names (FQDNs) that can be accessed from a vnet. Importantly, application rules aren’t applied for inbound connections; thus, to filter inbound HTTP/S traffic, Microsoft advises using a Web Application Firewall (WAF).
- NAT rules configure DNAT rules to allow incoming internet connections.
Microsoft notes some important Azure Firewall policies and rules to keep in mind:
- Inbound internet connectivity can be enabled by configuring DNAT as described in Microsoft’s “Filter inbound traffic with Azure Firewall DNAT using the Azure portal” process.
- In terms of outbound traffic, if you configure network rules and web application rules, then network rules are applied in priority order before application rules, and the rules are terminated. This means that no other rules are processed if a match is found in a network rule.
- If you have configured an intrusion detection and prevention system (IDPS), it will monitor and block suspicious traffic it catches.
- In HTTP and TLS-inspected HTTPS cases, the firewall ignores the packet’s destination IP address and uses the DNS-resolved IP address from the host header. The firewall expects to get the port number in the host header. Otherwise, it assumes the standard port 80.
- A port mismatch between the actual TCP port and the port in the host header will drop traffic.
- DNS resolution is done by Azure DNS or a custom DNS configured on the firewall.
How Tufin Can Help You Manage Firewall Rules
By using Tufin, you make sure simple logic is applied such that the rule base will not become too complex. Here are some key benefits of Tufin’s approach to firewall rules:
- Firewall change management helps you effectively manage firewall configuration changes, maintain your network security policy, and optimize the firewall rulebase. Tufin advocates and practices automation for firewall rule changes, which helps you avoid human errors and speeds up network changes.
- Implementing an automated solution such as firewall change automation simplifies the change process, ensuring fully automated network change workflows, which results in reduced SLAs. Tufin automatically identifies redundant rules and reviews and tests every access change against a company’s security policy rules.
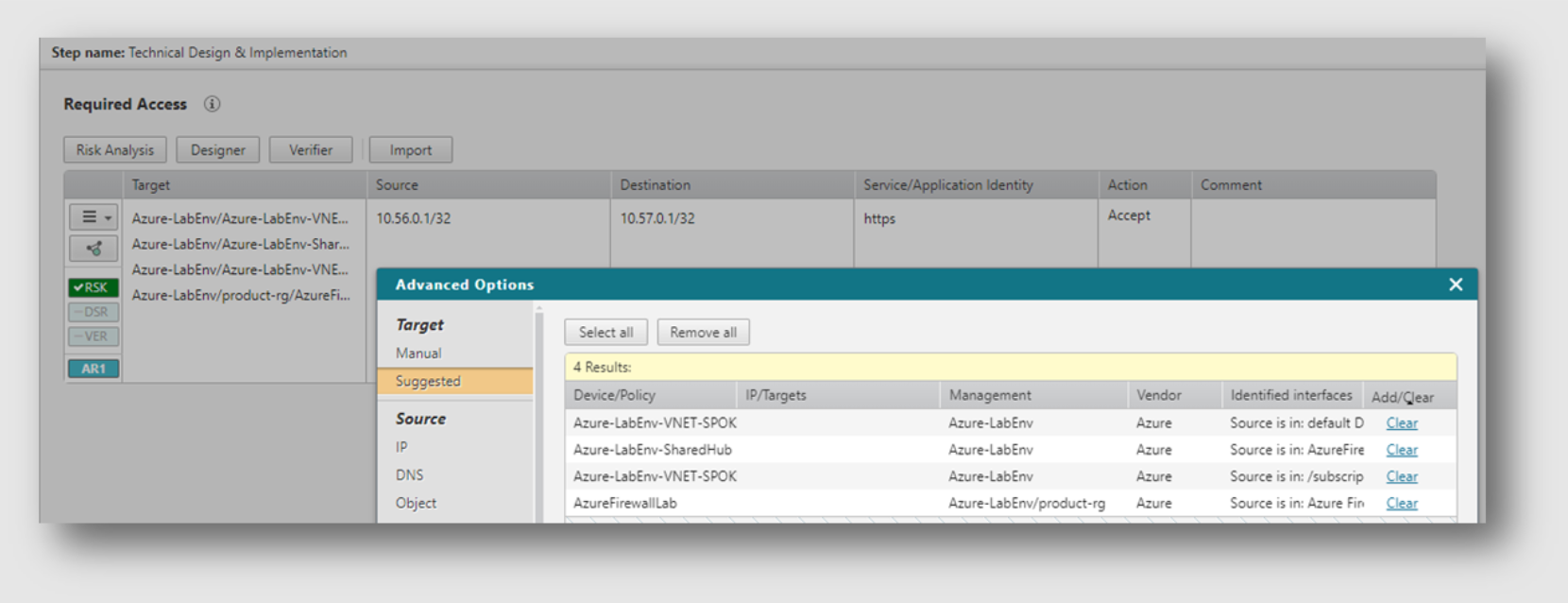
- Tufin’s approach to firewall change management ensures that changes to rulebases are tracked, approved, and implemented effectively. A change request will result in either a new rule or changing an existing one, thereby minimizing the chance of errors and policy violations.
- It’s also critical to perform regular firewall auditing to identify vulnerabilities, unused rules, or misconfigurations. Tufin’s software generates security audit reports on demand. Reports can be easily automated, based on criteria, such as business area, firewall vendors, cloud service providers, time periods, and geographic regions.
How Tufin Can Help Enhance Your Security and Access Policies
Tufin not only integrates with Azure Firewall but with all of your Azure cloud networks and tools, including Azure network security groups. Tufin seamlessly integrates Azure’s public cloud capabilities into a cohesive and automated network security policy management framework, ensuring that security policies are uniformly applied across diverse cloud environments and data centers.
Further, Tufin’s security policy change automation and enforcement capabilities build on top of native Azure network security features, providing enhanced visibility into your network topology. You can have live and automated mapping of your Azure Firewall and other Azure-based network assets and virtual machines, and can simulate traffic paths across your Azure and on-premises infrastructure. This allows your network security and IT teams to map out dependencies, analyze traffic flows and workloads, and optimize network performance.
Tufin’s integration with Azure automates the process of implementing network changes to reduce the time and effort required to make network changes. This is true for Azure Firewall rule changes as well as all your Azure resources.
To learn more about how Tufin can help automate and orchestrate your security, sign up for a live demo.
Ready to Learn More
Get a Demo





