«ROI on our Tufin investment has been great. It was, and still is, driven by productivity gains, reduction of re-work from manual errors and automated coordination across teams»
– Head of Firewall Management Team, Big 4 Professional Services Firm
Tufin lets your team do more with existing resources by providing flexible workflows and automation that can dramatically reduce your time spent on network changes and rule lifecycle management.
Repeatable, auditable and policy-driven processes also reduce risk for your organization, while making it easier for you to implement and maintain more advanced network segmentation.
Tufin integrates with leading ITSM solutions, allowing for a ticket in your ITSM to trigger a workflow within Tufin.
Workflow Examples:
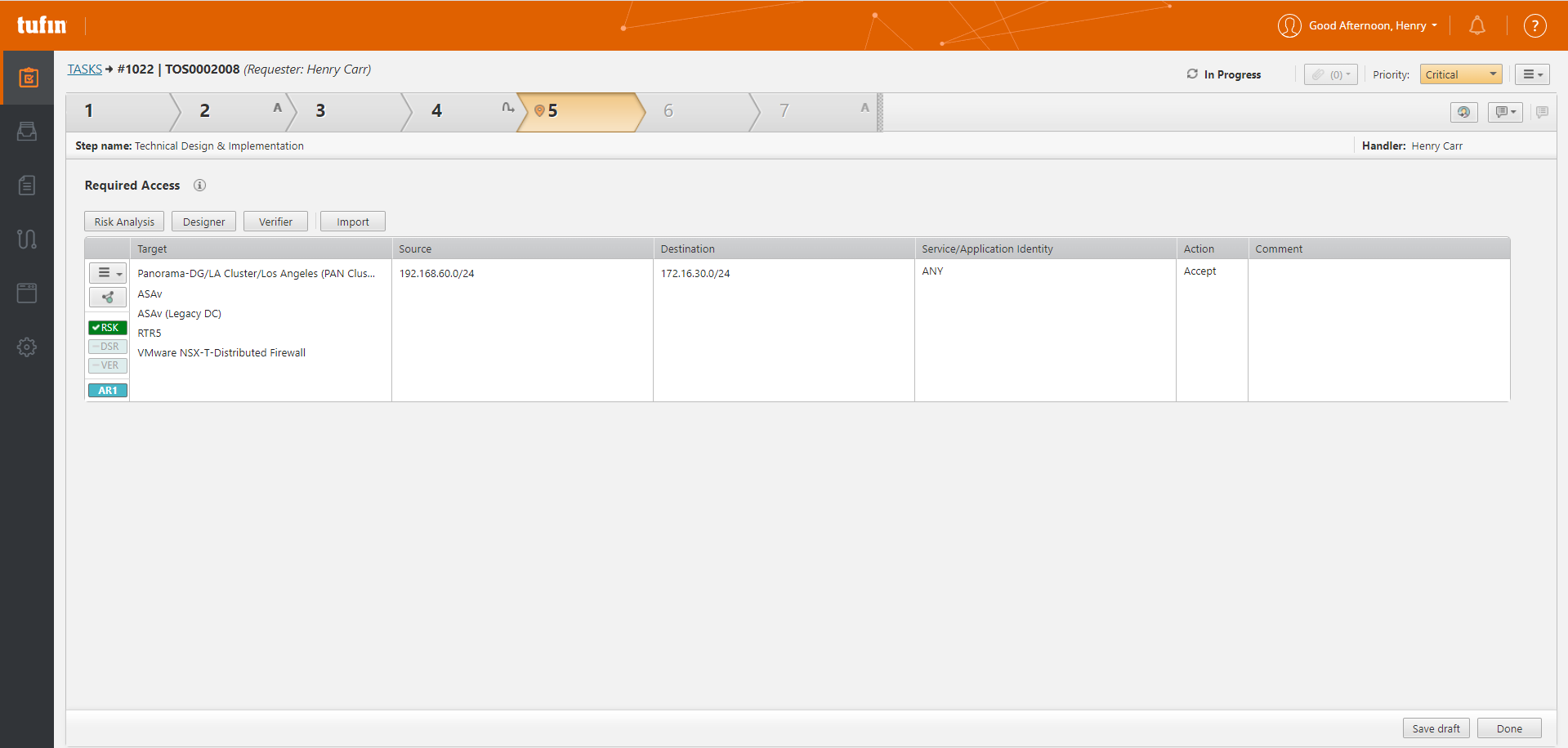
Use SecureChange+ or integrate with your ITSM to submit the requests with your ITSM
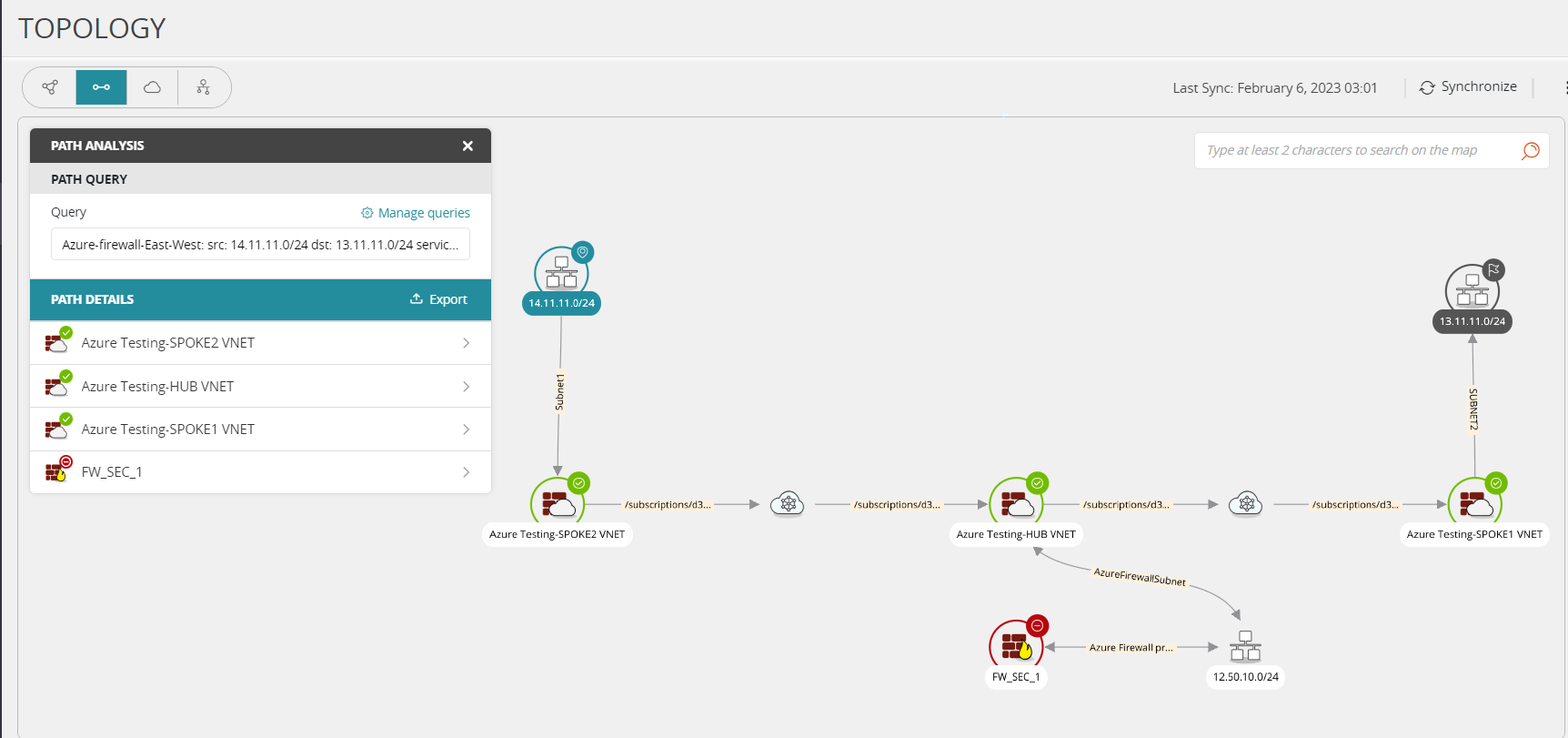
Automatically identifies firewall targets and security groups based on real-time, full path analysis of your network
Automatically performs risk assessment against the policy, vulnerability data and other third-party security intelligence to avert policy change violations and prevent access to risky assets
SecureChange+ automatically suggests the most efficient set of changes necessary across network devices and security groups to process a request ticket
The Verifier automatically tests to confirm that your change was implementated
All changes made are documented and reportable
Tufin orchestrates rule review across owners with an automated recertification process. It identifies expiring or expired rules and maps them to owners, eliminating many of the manual steps normally required.
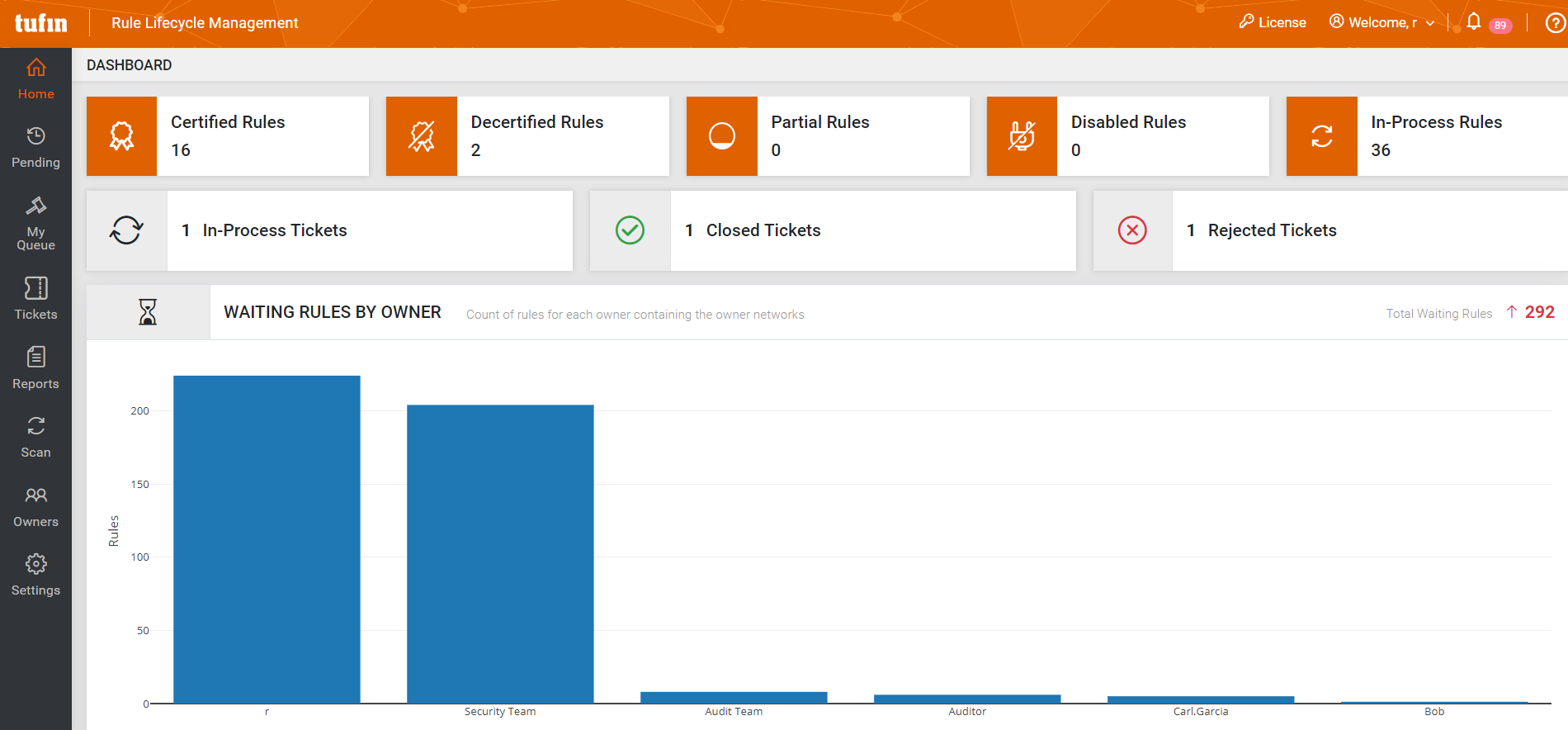
SecureChange+ topology intelligence and dynamic mapping powers many of the capabilities that set Tufin apart from the competition.
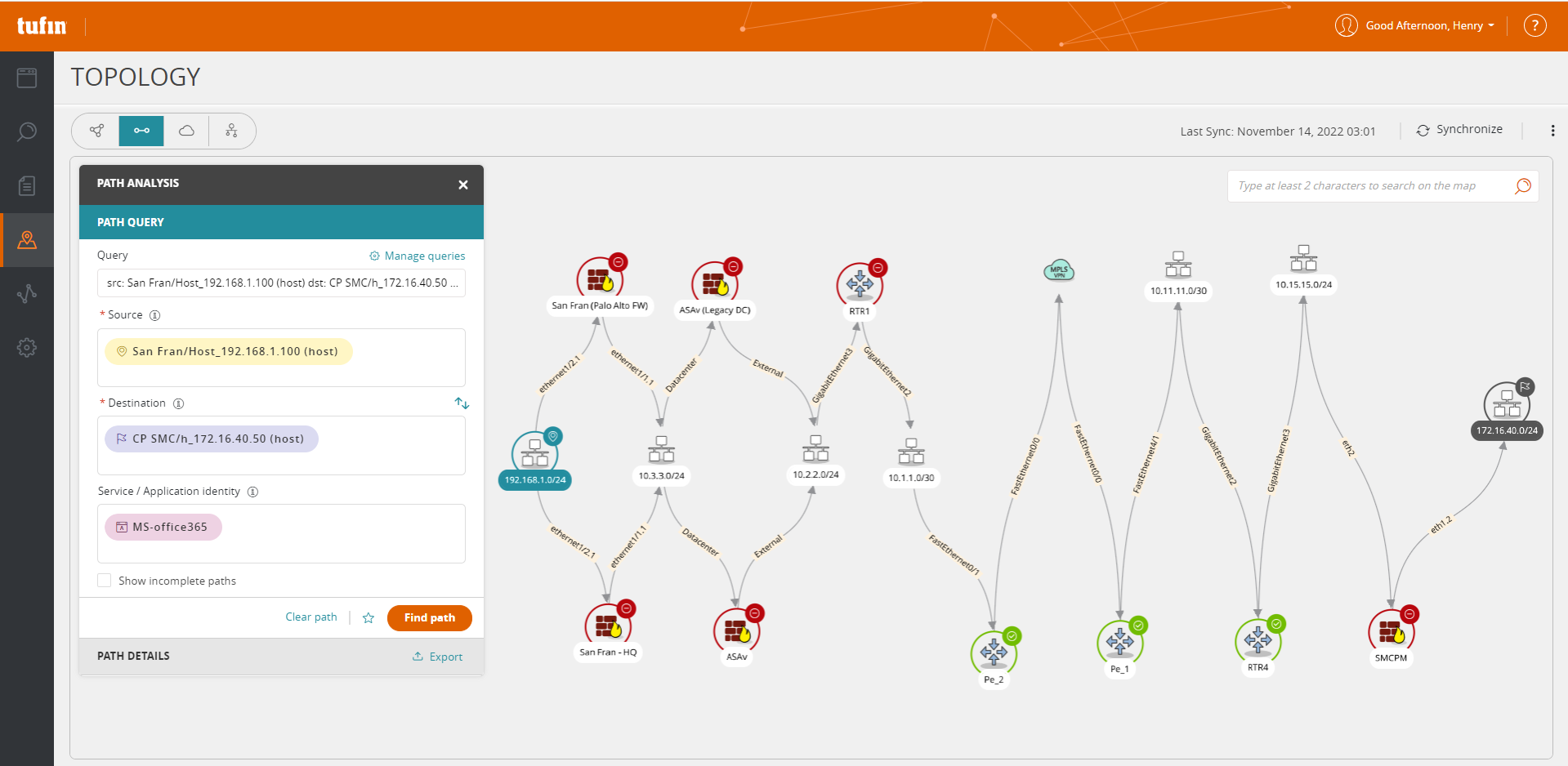
SecureChange enables continuous compliance with internal policies and industry regulations, such as PCI-DSS, NERC-CIP, and HIPAA.
Proactive risk assessment is part of the network change design process. This vets proposed changes against your security/compliance policies, and it can be customized to cross-reference intelligence from third-party solutions, such as vulnerability management tools, SIEM, SOAR and endpoint threat detection tools.
Only Tufin provides agentless, multi-cloud policy management. Take full advantage of cloud-native infrastructure, maintain enterprise-wide visibility and control, and optimize segmentation across on-prem and cloud.
Integrate security guardrails into the CI/CD process.
Tufin easily integrates into your CI/CD process to serve as the security gatekeeper for your DevOps team, so they don’t need to change how they work. Tufin will alert on access changes that violate segmentation policies and proactively block the changes pre-deployment. This simple step can vastly reduce risk for your organization while trimming workload.
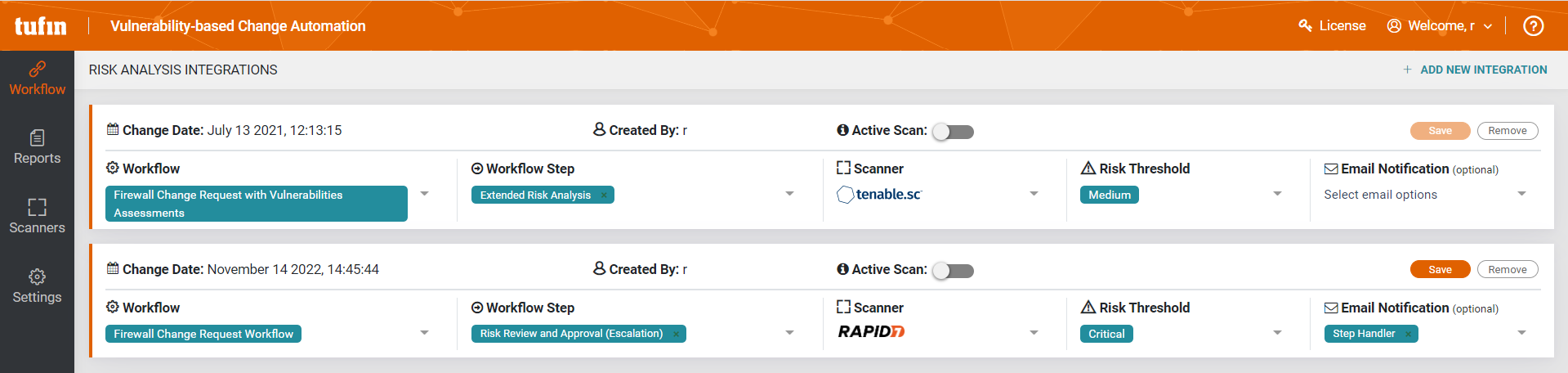
Vulnerability-based Change Automation (VCA) integrates vulnerability awareness into the change design process, by checking for vulnerabilities on source and destination during the change design process.
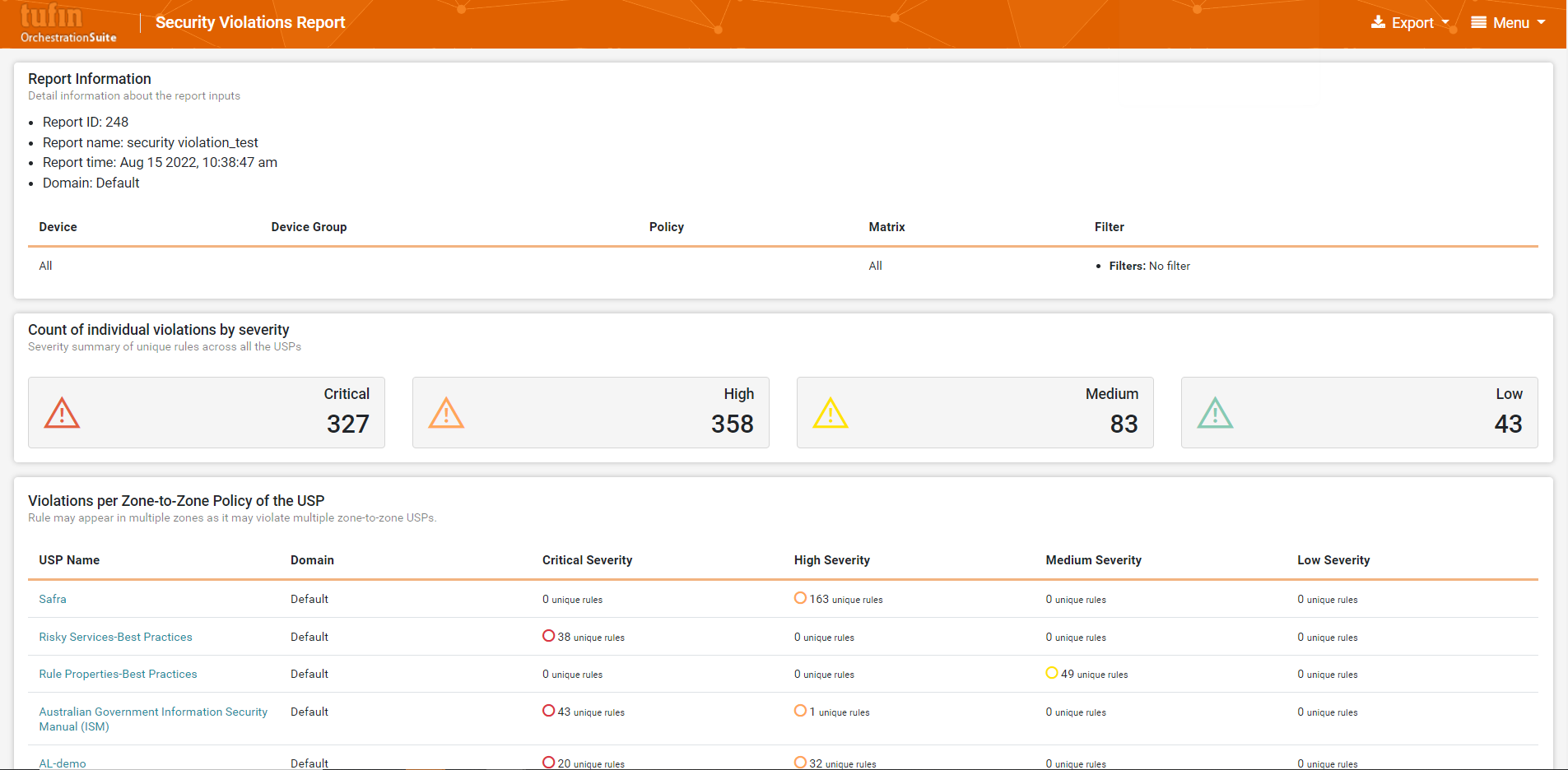
As with SecureTrack+, SecureChange+ provides real-time compliance monitoring and a variety of customizable audit reports that align with regulatory standards, such as PCI-DSS, NERC-CIP, HIPAA, GDPR and more. However, SecureChange+ enables a more advanced state of audit readiness by providing a comprehensive audit trail for network changes, including full change accountability and audit-ready reports. All related tickets and every change is logged and reportable.

Only Tufin provides automation and a unified security policy, from on-prem to cloud, across NetSec and DevOps.