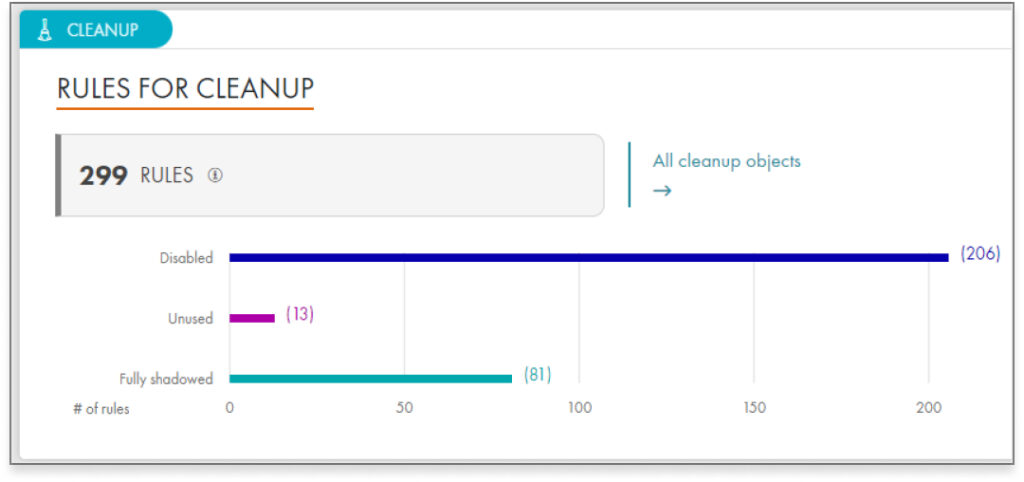
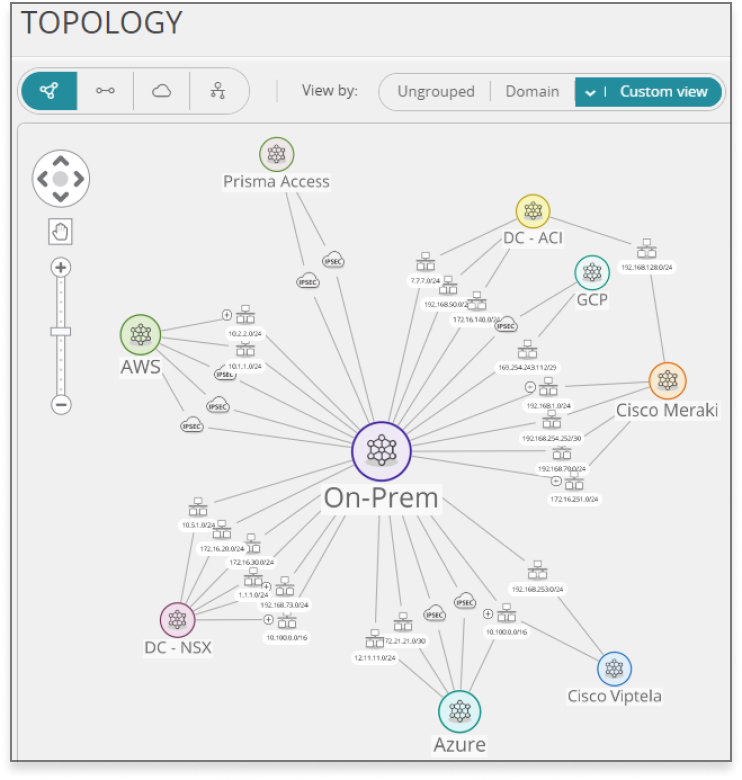
Beyond automation, enterprises should look for a firewall analyzer that supports multi-vendor firewall devices, including next-generation firewalls (e.g., Cisco, Fortinet, Juniper, Palo Alto Networks, Check Point, SonicWall), as well as multiple cloud providers (e.g. AWS and Azure). It should provide real-time reports of policy violations, including reports that demonstrate compliance with critical regulations and standards, such as PCI-DSS, HIPAA and GDPR. Mre advanced security policy automation solutions, like Tufin, enable api integration with vulnerability scanners to help teams prioritize vulnerabilities, further reducing the risk of cyberattacks.