Security Operations teams face a daily battle, fighting through a myriad of security events in an effort to find that one which could be indicative of a major security incident. SecOps teams do not lack information; SIEM, XDR, CMDB, vulnerability management, threat intelligence, IDS/IPS, identity management, and many other solutions can provide data relevant to potential security incidents. What SecOps teams often lack, however, is the time required to gather information for each event and turn this raw, unrelated data into actionable insights required to properly detect and respond to advanced threats. An increasingly distributed workforce, the ever-expanding array of security solutions, and the move to cloud and microservices, are just a few additional complications which have exacerbated this challenge over the past several years. To continue to effectively secure the enterprise and minimize risk, enterprises are increasingly turning to orchestration and automation as a force multiplier. Orchestrating and automating repeatable security processes enables SecOps teams to focus cycles on more advanced tasks, utilizing their most valuable resources, well trained and experienced analysts, more effectively and efficiently.
ServiceNow, a staple among global enterprises, delivers a unique orchestration and automation solution: ServiceNow Security Operations. Security Operations provides enterprises with a wide range of capabilities to increase operational agility and build cyber resilience. Our focus today will be on workflow management through Flow Designer, but you can find more information about other features of Security Operations here. Flow Designer allows enterprises to codify complex security and incident response processes into repeatable workflows that can be automated to enrich, correlate, and add context to security event information. How does Tufin add value? Tufin has been the leader in security policy management for over a decade, providing visibility into and management of some of the most complex, heterogeneous networks in the world. Tufin’s knowledge of network security policies and topology can provide unique network insights to SecOps teams and automated processes, allowing for more accurate triage and risk assessment decisions. Tufin’s new ServiceNow connector delivers these capabilities directly to the hands of SecOps teams through Flow Designer, allowing enterprises to leverage this information throughout the entire event lifecycle.
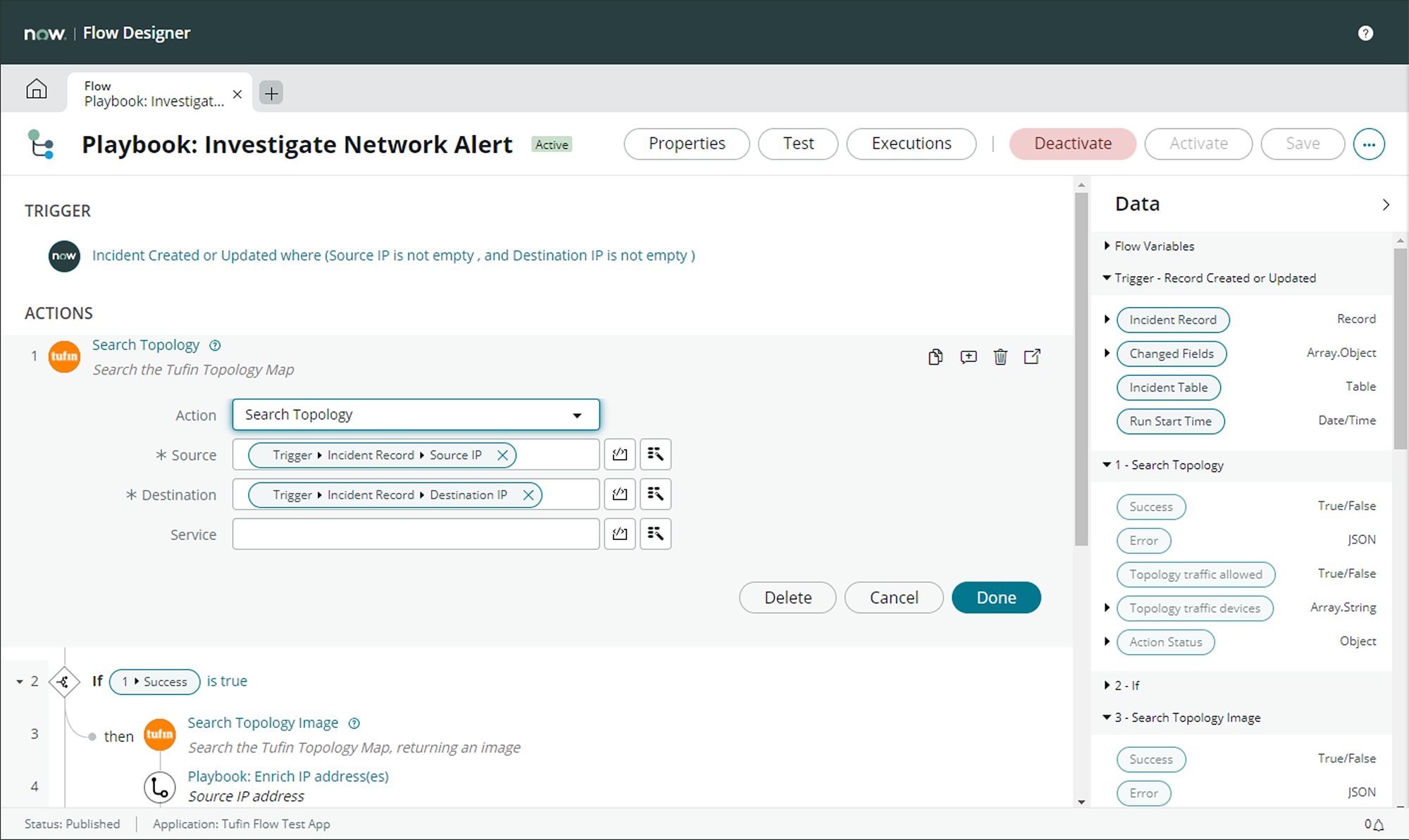
Table A: Example Flow Designer Workflow
Context-Based Triage
Let’s walk through an example of how SecOps teams can leverage Tufin to automatically triage and respond to a potential security incident. We’ll use an IDS alert, an event which may be received dozens or hundreds of times per day and often contains only very basic information, such as source and destination IPs and ports, and signature information. Tufin can provide valuable insights into the source and destination addresses. For example, what network objects are these addresses related to? What zones are these addresses related to? If the source or destination address is related to an object or zone which is a part of the enterprise’s PCI environment, for example, automatic escalation may be appropriate.
But what security policies are relevant to these source and destination addresses? Perhaps the single most valuable insight Tufin can provide comes from our in-depth knowledge of the network topology. With just the source and destination IP addresses and ports, Tufin can determine not only the path the suspicious traffic would have taken, but also whether the traffic would have been permitted or denied. If the traffic was denied by policy, perhaps the event can be deescalated. If the traffic was permitted, escalation may be appropriate.
Threat Containment
When it comes time for threat containment, Tufin and ServiceNow have that covered as well. While it is possible to provision network changes with Flow Designer through direct integration with many of the major network security solutions, this approach has some drawbacks. In very complex, heterogeneous networks, it is almost impossible to codify a process to determine where a single change will need to be made and what vendor technology will be involved. Such changes are also blind to existing rules, compliance requirements, and their impact on the overall policy base.
Tufin utilizes knowledge of existing policies and network topology to intelligently design changes across a hybrid, heterogeneous network; and it’s all available through Flow Designer. Creating a new policy to block the suspicious traffic from our IDS alert is as simple as submitting a single request via an automated workflow.
Once the request is submitted, it will be handled according to the enterprise’s established change control processes. Considering existing policies and network topology, Tufin designs optimized changes, creating new rules only in the locations and devices on which changes are required. The design and provisioning of these changes can be fully automated, or incorporate analyst oversight, as needed.
The best part? This integration is absolutely FREE!
You can download the Tufin integration from the ServiceNow store here. The ServiceNow Security Operations integration with Tufin provides SecOps teams with unparalleled visibility into security policies and topology directly from ServiceNow. Integrating with Tufin allows ServiceNow workflows to make more accurate automated decisions based on the current state of access and connectivity, reducing analyst workload and security incident response times. Tufin’s industry-leading change management solution allows enterprises to perform rapid threat containment across a hybrid, heterogeneous environment, while ensuring auditability and compliance is maintained throughout the event.
- Home
- Blog
- Network Security Automation
- Accelerate Incident Triage and Response With ServiceNow










