Reduce Your Attack Surface
Zero Trust starts with reducing exposure. But in today’s fragmented, fast-changing networks, the attack surface is constantly shifting and difficult to control. Reducing the attack surface is about minimizing entry points, tightening security policies, and enforcing access control across endpoints, systems, and hybrid environments.
Tufin delivers a unified control plane giving security teams centralized visibility, risk-aware prioritization, and automated enforcement to contain exposures and align with Zero Trust principles. By combining full attack surface visibility, context-aware prioritization, and automated workflows, Tufin helps organizations shrink the attack surface, reduce security gaps, and cyber threats across hybrid environments.
Assess Critical Risks Quickly
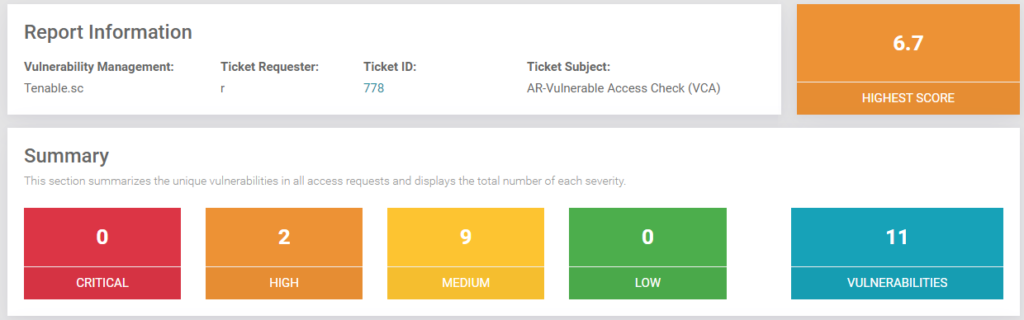
Get immediate clarity, through attack surface management. Tufin unifies vulnerability management data and posture insights so you can spot, prioritize, and act on the exposures that matter most.
- Consolidate vulnerability and posture data into a single dashboard for end users.
- Enrich scan results with authentication, connectivity and exposure insights
- Pinpoint exploitable, high-impact vulnerabilities and attack vectors
- Track remediation progress to measure risk reduction
Prioritize Vulnerability Remediation
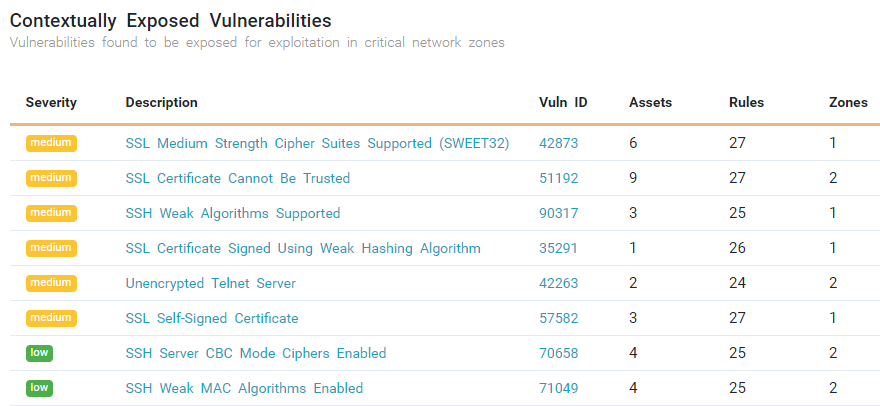
Stop wasting time on noise. Tufin ensures remediation efforts focus on the vulnerabilities that are both exploitable and high-risk.
- Validate whether vulnerabilities are actually reachable
- Focus remediation where the greatest risk exists
- Automate vulnerability-aware access changes to accelerate patching
- Orchestrate remediation directly from a single control plane
Automate Risk Mitigation
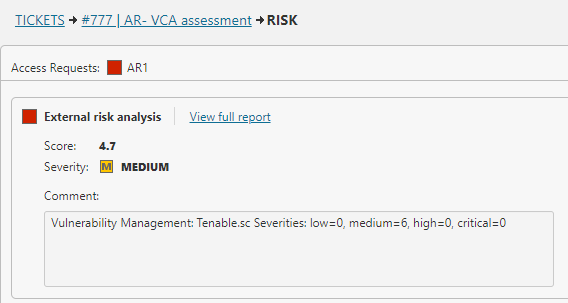
Shrink your attack surface with automation and endpoint security enforcement. Tufin encompasses security measures and group policy to block risky access, ensuring the correct permissions are in place to enforce Zero Trust controls, before exposures can be exploited.
- Automate policy changes across firewalls, cloud, SASE, and hybrid environments
- Block access to vulnerable systems until patching is complete
- Prevent risky new access requests before they are approved
- Enforce Zero Trust segmentation automatically to contain lateral movement
How Tufin Delivers Attack Surface Reduction
The Tufin Platform is a comprehensive, AI-driven unified control plane for network security policy management. The platform is comprised of:
SecureTrack+
See every risk before it becomes a problem — with unified visibility, accurate topology mapping, and continuous risk assessment across firewalls, cloud, SASE, and microsegmentation. Automate policy optimization to reduce exposure and ensure continuous compliance.
SecureChange+
Turn slow, error-prone changes into secure, automated workflows. Accelerate delivery and cut SLA times by up to 90% with automated design, rule lifecycle management, and hybrid connectivity troubleshooting that eliminates delays and misconfigurations.
Enterprise
Scale security without slowing innovation. Automate access provisioning, accelerate application connectivity, and ensure uptime with built-in high availability and global scalability for the largest, most complex networks.
Attack Surface Reduction with Tufin
With Tufin, organizations stop chasing endless patch lists and start focusing on exposures that truly matter. The result: fewer breaches, lower risk, and faster remediation, and all managed through a single control plane.
FAQs
Reducing the attack surface means lowering the number of entry points and attack vectors that hackers can exploit. It involves tightening security policies, cleaning up unused firewall rules, hardening the operating system, and removing unnecessary permissions or business applications. By doing so, organizations reduce opportunities for cyber threats like ransomware, malware, and phishing to succeed. Effective attack surface reduction improves overall cybersecurity resilience for both endpoints and end users.
Tufin provides continuous visibility into firewall and security policies, helping organizations identify unused, shadowed, or overly permissive rules. By cleaning up policies across hybrid and cloud environments, we reduce the attack surfaces while keeping security aligned with business needs.
Organizations use a combination of security tools and operational practices to reduce attack surfaces:
- ASR rules are attack surface reduction rules that block risky behaviors, such as malicious macros or untrusted executable files in office applications
- Endpoint security capabilities such as EDR, antivirus, and exploit guard for real-time protection against cyber threats
- Centralized enforcement of security policies and access control across hybrid environments
- Ongoing patching, vulnerability management, and removal of unused business applications or exposed APIs
- Strong authentication and least-privilege permissions to minimize unnecessary access
Tufin complements endpoint security by reducing risks at the network layer. We automate firewall rule changes while ensuring compliance with corporate security policies. This enforces consistency across hybrid environments, eliminating misconfigurations that expand the attack surface.
Attack surface reduction works by preventing risky activities and tightening controls before attackers can exploit them. Examples include:
- Blocking suspicious child processes from office applications
- Preventing credential stealing from sensitive processes such as lsass
- Detecting malicious macros and stopping untrusted executable files
- Using audit mode to monitor policy effectiveness, track event logs, and reduce false positives
- Enforcing endpoint security controls such as EDR and exploit guard, with notifications and remediation workflows for quick response
Tufin provides real-time visibility into risky access paths and policy misconfigurations. Combined with automated workflows, we reduce the chance of overly permissive firewall rules that could be exploited, ensuring organizations can enforce ASR strategies consistently.
Exclusions should be created only when strictly necessary, as they expand the attack surface. A structured process helps:
- Start in audit mode: Review the event log to determine if alerts are legitimate or false positives.
- Validate legitimacy: Confirm the application is a trusted business application and essential for operations.
- Minimize scope: Apply exclusions narrowly to specific end users, files, or processes.
- Document and review: Keep a record of all exclusions and enforce regular reviews.
- Favor remediation: Adjust security policies, permissions, or configurations rather than relying on long-term exclusions.
Tufin helps organizations safely handle policy exceptions with automated approval workflows and built-in risk checks. Instead of creating broad exclusions, security teams can implement narrow, controlled changes that preserve compliance while supporting legitimate applications.
- Apply ASR rules: Enforce attack surface reduction rules to block risky child processes, suspicious macros, and malicious executable files.
- Strengthen endpoint security: Use EDR, antivirus, and exploit guard for real-time defense.
- Centralize policies: Standardize security policies, access control, and authentication across environments.
- Maintain hygiene: Conduct continuous patching, vulnerability management, and removal of unnecessary business applications and APIs.
- Adopt zero trust: Use segmentation and least-privilege permissions to limit attacker movement.
- Refine continuously: Run audit mode, monitor notifications, and tune policies to reduce false positives while protecting against cyber threats.
Tufin ensures continuous compliance and visibility, while automating enforcement of best practices at scale. This reduces the risk of human error in firewall and cloud policies, a critical factor in minimizing the attack surface.
- Policy-driven controls: Implement attack surface management programs with automated workflows and security measures.
- Endpoint protection: Standardize EDR, antivirus, and exploit guard across all endpoints and operating systems.
- Identity and access security: Strengthen authentication, enforce least-privilege permissions, and monitor for credential stealing attempts.
- Operational rigor: Prioritize patching, ongoing vulnerability management, and structured remediation to reduce exposure.
- Hybrid visibility: Extend security policies across on-premises and cloud environments, integrating through API connections.
- Continuous monitoring: Leverage event logs, notifications, and audit mode to measure effectiveness and adjust over time.
Tufin delivers end-to-end visibility and control across hybrid and cloud environments. By unifying policy management and automating enforcement, we reduce complexity, accelerates remediation, and ensures attack surface reduction strategies are applied consistently across the organization.
Additional Resources
Learn more about how Tufin automates vulnerability management to prioritize safeguarding against the most critical risks.
Firewall Management Resources
Articles
Solutions
Get Started with Tufin
See how Tufin unifies vulnerability management, segmentation, and posture control to reduce your attack surface and strengthen Zero Trust initiatives.



