Comply with least privilege access requirements by implementing and enforcing segmentation.
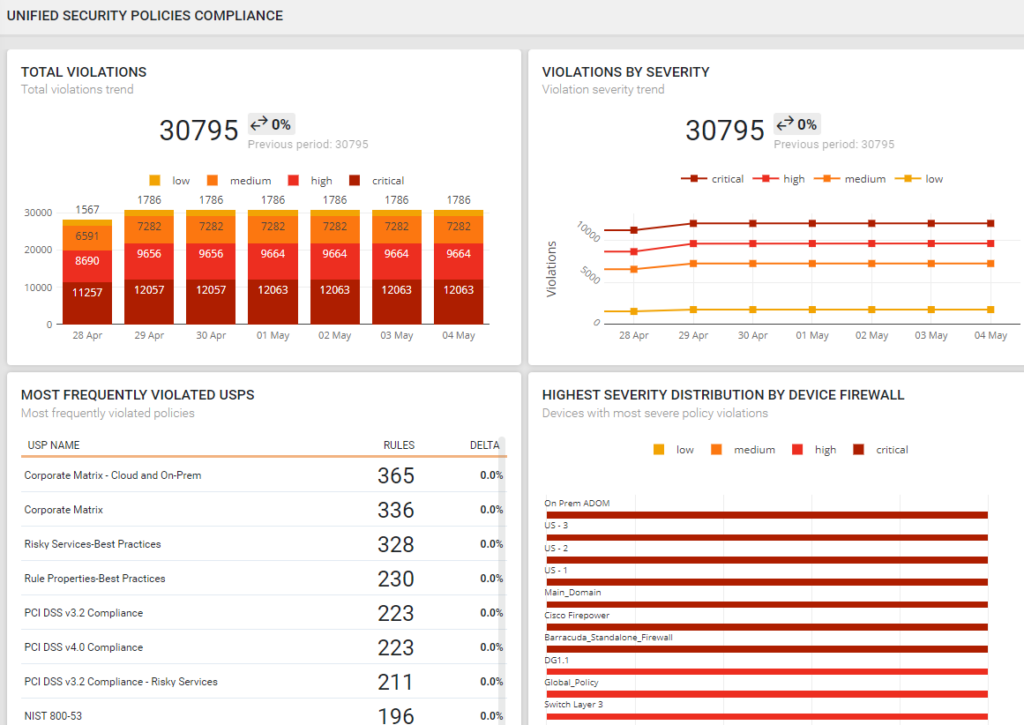
Meet compliance objectives by automating documentation collection and reporting.
Lower third-party audit costs with enhanced reporting capabilities.
Proactively analyze risks within automated change workflows.
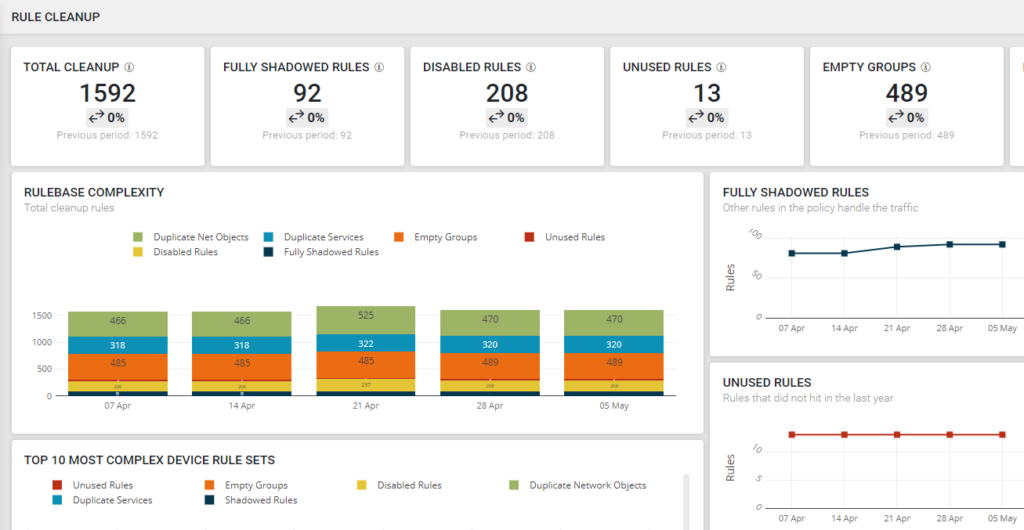
Reduce complexity by identifying and decommissioning unnecessary rules.
Enhance compliance with improved incident response.
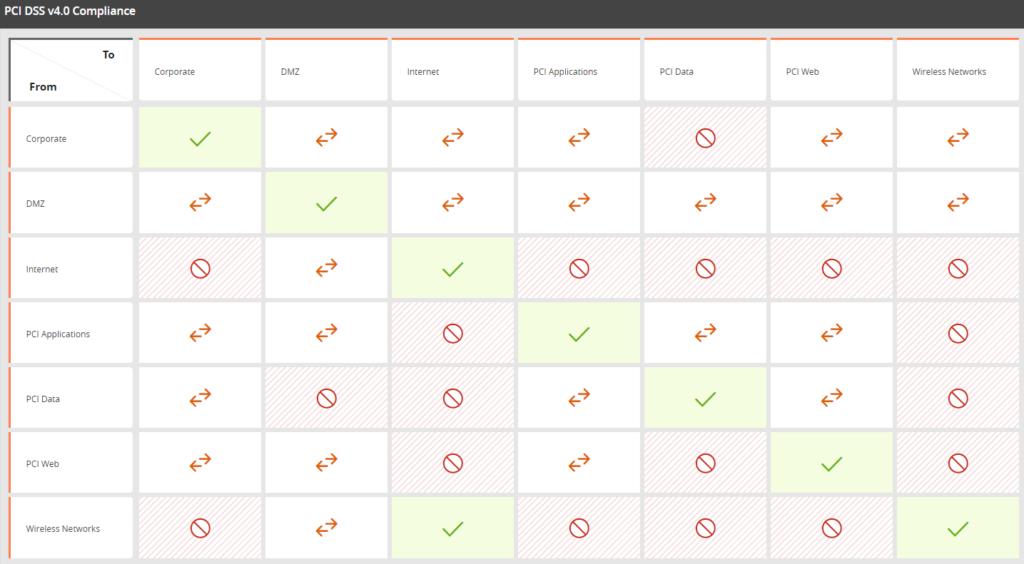
Achieve compliance with network segmentation requirements across your hybrid environment by implementing vendor agnostic segmentation polices then automating the monitoring and enforcement.
Develop and easily manage standardized security policies across legacy firewalls, next-generation firewalls (NGFW), SDN, SASE, and Edge devices.
Automate documentation request processes with reports and change management tracking so teams can focus on high-value tasks.
Proactively analyze risk and automate change management before implementation.
Cleanup and optimize firewalls by identifying unnecessary rules and aligning security policies with business objectives.
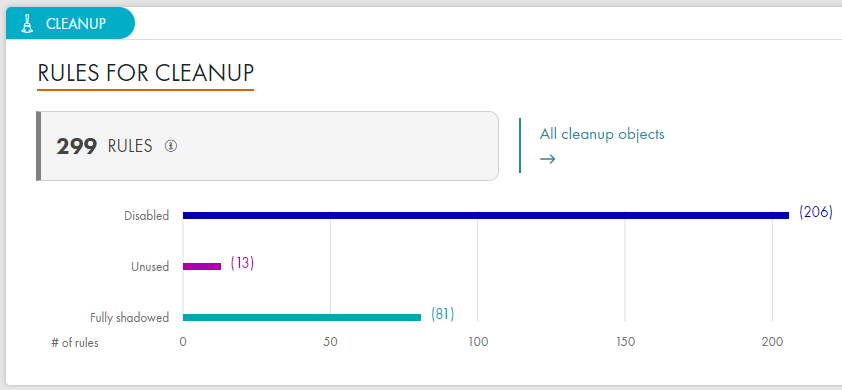
Improve key metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) to reduce financial exposure and minimize compliance violation risks.
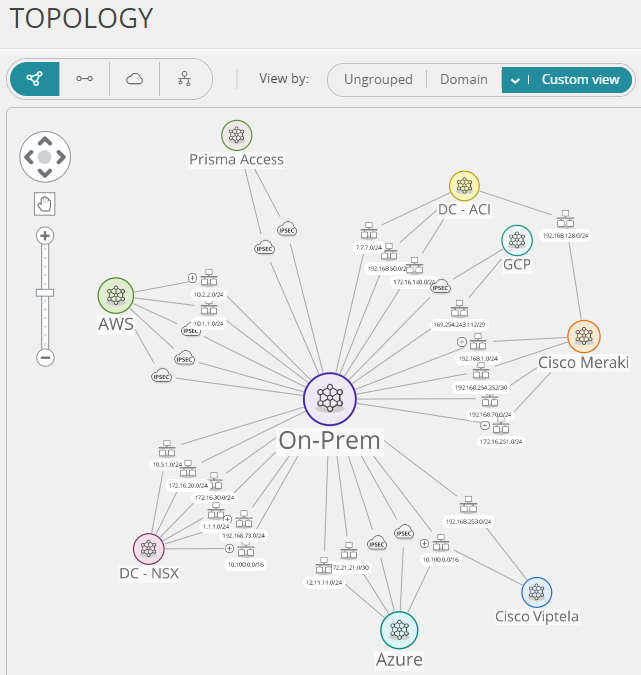
Learn more about Tufin’s ability to streamline audit documentation and reduce costs.



Elevate your network security and cloud security operations with Tufin's product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.