Welcome, Adventurer. Traveling the path of network security can seem as overwhelming as embarking on a quest filled with dragons and evil wizards. However, as with any adventure, having the tools necessary to battle adversaries is critical. Tufin’s network security offerings help you uplevel your network security by giving you the capabilities you need when you need them.
As we begin our journey together, choosing the Tufin solution that achieves your network security goals means understanding the difference between our SecureTrack+, SecureChange+, and Enterprise offerings.
SecureTrack+: A Basic Healing Spell
Just like an adventurer beginning a quest, your journey to network security may require an immediate fix to heal compliance or firewall rule wounds. Battling divergent network security policies feels like battling against a horde of small, venomous spiders. As the policies propagate, your attack surface expands, and your team becomes enmeshed in a million small fights against vulnerabilities and tedious reports.
SecureTrack+ helps your team heal the wounds caused by battling network security monsters with flexible, easy-to-maintain Unified Security Policies (USPs) based on your unique environment. With USPs, teams can maintain consistent network access controls across even the most complex environment, enhancing compliance with continuous monitoring, reporting, and trends analysis. With SecureTrack+, you get:
- Monitoring to manage network performance, communications, and change tracking.
- Reporting for compliance documentation, compliance trends, risk reduction, continuous audit readiness evaluation, and vulnerability exploitability.
- Compliance management with zone-based USPs, individualized security policy builder, continuous security policy management, native integrations with GRC tools.
- Automation consisting of server policy cloning to support migration, server decommissioning, and rule decommissioning.
Through the combined power of USPs, automation, and reporting, you can create, document, and enforce the network security controls necessary to achieve your compliance and audit goals. Enforcing the principle of least privilege in heterogeneous environments feels overwhelmingly time-consuming when you need to compare and contrast different naming conventions and levels of granularity.
Tufin heals these pain points by giving you a single management console with policies that simplify security policy management. By maintaining rule cleanup, you reduce your attack surface while gaining rapid insight into potentially exploitable vulnerabilities. Combining this with automation means that you can streamline your compliance processes for a comprehensive approach to network security.
SecureChange+: Observing the Quest Landscape
Every adventurer journeys beyond their home base with quests that bring them to new lands while bringing with them the tools already accumulated. Similarly, your network security adventure will bring you beyond your basic network configurations. With multiple segments bounded by multiple firewall vendors, your complex network environment can include on-premises and cloud-based deployments. On your journey, a map guides you through the landscape and can alert you to new risks.
SecureChange+ gives you the deep network visibility necessary for understanding how devices impact each other, minimizing vulnerability exposure, and achieving continuous compliance. From documenting and certifying rule ownership to rapidly troubleshooting network connectivity issues, SecureChange+ provides all the capabilities of SecureTrack+ then adds:
- Topology mapping for network visibility, target selection, path analysis, and network connectivity troubleshooting.
- Automation for network access decommissioning, rule and group modification, and network access requests.
- Rule lifecycle and ownership capabilities with rule recertification and rule lifecycle management.
Modern networks are labyrinths of data flows and connections. Just like a wrong turn in a dungeon can bring you to a monster, a change to a network configuration can create new risks.
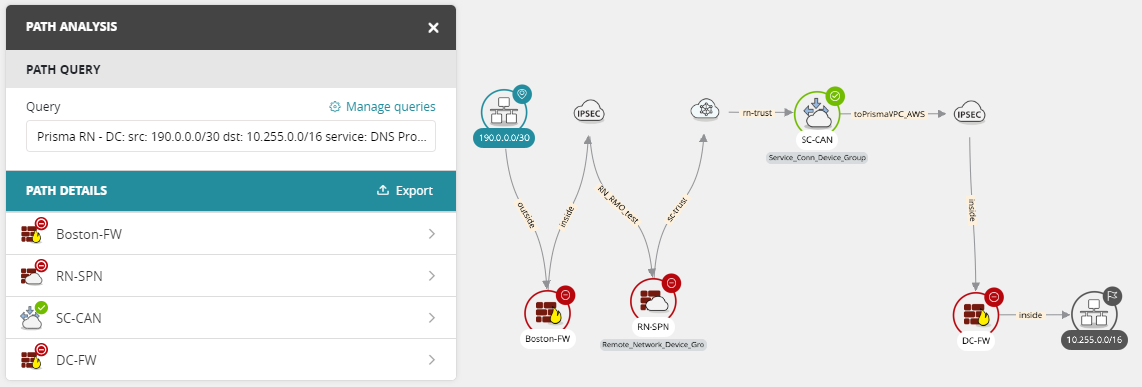
Tufin’s toppology maps ensure that network change requests are accurate and effective, automating the risk analysis process to prevent security and operations issues. As part of accepting your network security mission, you need visibility into how data travels across your networks and insights into how attackers can move through them. Tufin’s Topology provides this visibility so you can shut down connections rapidly to mitigate the risk of lateral movement. However, you need to keep networks functioning as much as possible.
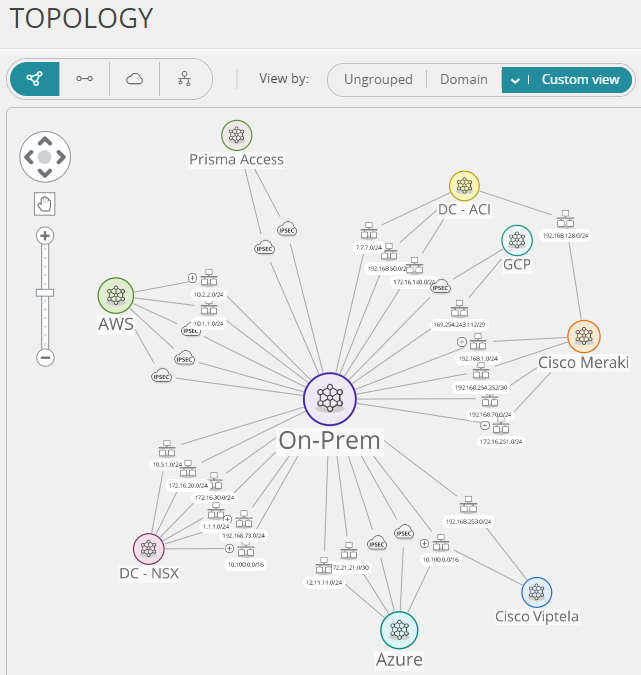
To improve response times, you need to identify paths attackers could follow when trying to move across networks and assets. With Tufin’s Topology Map, you can analyze these paths quickly and uplevel your security operations center (SOC) response capabilities.
Enterprise: Finding the Hidden Treasure
Adventuring is about more than fighting evil or exploring new realms. As the hero in your network story, you search through the caverns of connectivity to find the hidden treasure of application access and network change automation. The solution you seek at this level enables you to onboard applications and make change implementation rapidly and securely so that your business can achieve the financial benefits they bring.
Tufin’s Enterprise solution enables you to achieve zero-touch automation that implements changes in minutes rather than days. The hidden treasure with Tufin Enterprise lies in the 94% efficiency improvements you can achieve with our network change analysis and implementation. When combined with the 95% efficiency improvements for audit preparation and reporting, you can save $5 million – a true adventurer’s bounty.
As the only Tufin solution that allows you to build application specific security policies, Enterprise offers the most capabilities and features for streamlining network and firewall management., Enterprise starts with the foundation of SecureChange+ then extends it to include application-based connectivity management with:
- Application-centric security policy generation
- Application dependency mapping
- Application mapping to firewall rules with owners
As a network hero, your agility keeps your business moving in the right direction by ensuring that it meets time-to-market goals without compromising security. Once you define the applications and configure connections, Tufin’s network topology intelligence provides end-to-end visibility and continuously displays connectivity status so that our diagnostic tools can help you understand, troubleshoot, automatically repair connectivity issues, and maintain continuous compliance.
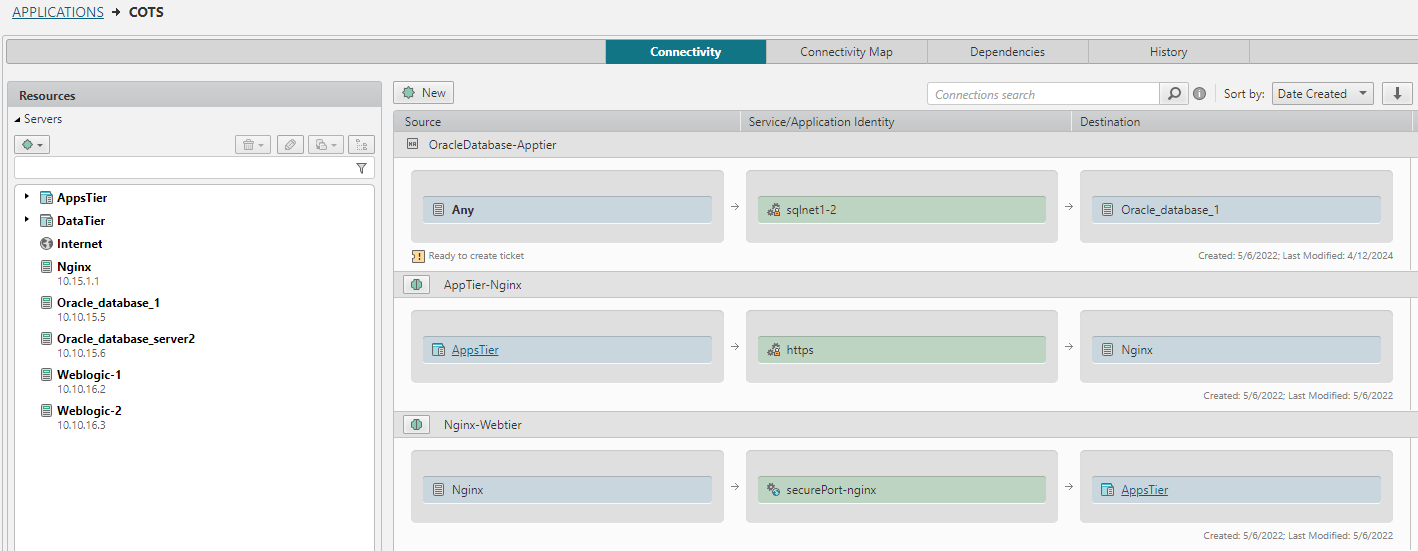
You can become a security change and application discovery wizard with the click of a mouse. Tufin’s central repository holds all application connectivity requirements and gives you the magic “one click” touch for:
- Automating the change management and risk analysis process so you can define, implement, monitor, maintain, and decommission application connectivity.
- Gaining real-time visibility into business applications’ connectivity requirements, status, and access change tickets.
- Automating application discovery by analyzing firewall revisions and network traffic linked to a server’s IP address.
As any adventurer knows, weathering disasters requires preparedness. You would never walk into a goblin den without having your most trusted support team, and the Tufin Enterprise level has your back. Our dedicated premium support team offers 24/7 call handling, troubleshooting, and problem resolution, the rangers with their long-distance arrows to back you up during a fight. With our high availability and disaster recovery capabilities, you have the protection that maintains network availability.
Tufin: “I Cast Firewall!”
For most adventurers, casting fireball quickly and efficiently obliterates enemies by covering a wide swath of landscape. On your network security quest, you need an equally powerful solution that spans network security, network operations, and cloud security. You can take Tufin on your journey, no matter where you start. With our tiered offerings, we meet you where you are while having capabilities that grow with you so you can achieve your goals and scale your operations as needed.
To start your adventure, contact us for a demo today.

Don't miss out on more Tufin blogs
Subscribe to our weekly blog digest











