Your networks are the freeway that deliver information across and from your company. Just like you hate getting stuck in bumper-to-bumper traffic, your workforce hates having slow connectivity that makes easy tasks take forever. Meanwhile, if you don’t implement the appropriate network security controls, your business can become the digital equivalent of an overturned tractor trailer burning on the highway. Not only is this dangerous, but it stalls productivity just like a major traffic jam.
To stay competitive, you transformed your business and embraced cloud-delivered applications and solutions that significantly impact network security policy implementation. To keep network traffic trucking along, you need to adapt your network security policy management (NSPM) processes, so they are flexible. However, in hybrid environments, differing security protocols and configurations create additional challenges as network administrators, IT teams, and security teams may lack consistent security measures across on-premises and cloud-based systems.
To cost-effectively manage these changes, you need a network security policy management solution that provides network visibility and automates key processes. Simultaneously, you remain confined by financial and staffing limitations.
A network security policy management solution is how your business keeps those digital roads safe and pot-hole free. Tufin’s automation reduces the time your teams spend managing repetitive tasks while enhancing network performance and improving IT security.
Ultimately, investing in a network security policy management solution provides long-term value across IT, compliance, risk, and operations.
What is network security policy management (NSPM)?
Network security policy management (NSPM) safeguards sensitive data and improves cybersecurity through the development, implementation, and maintenance of security policies that govern an organization’s IT infrastructure.
Network security policies help manage:
- Acceptable use of networks and systems
- Response to threats and security incidents
- Application and network access
- Vulnerability monitoring and patching by risk to the network
- Proactive risk mitigation
Additionally, many compliance mandates, most of which promote zero trust architectures, require network security controls. NSPM is critical to compliance with legal and regulatory frameworks like:
- GDPR
- HIPAA
- PCI DSS
- NERC CIP
- ISO 27001
- NIST 800-53
Why is NSPM important?
Network security policy management protects networks and sensitive data while enabling you to achieve business objectives by:
- Defining protocols for protecting assets
- Ensuring workforce members understand cybersecurity hygiene
- Implementing and enforcing security controls to achieve data protection compliance goals
- Identifying, assessing, and responding to evolving cyber threats and vulnerabilities
- Mitigating reputation and financial risks related to cybersecurity incidents and data breaches
How does network security policy management improve business operations?
Your business operations rely on your network’s security and its speed. If your network security slows down user access to resources, then the protections impact your financial bottom line. The good news is that network security policy management solutions can also help you improve network performance and daily operations.
Cost savings
Network administrators and IT teams find themselves spending time on repetitive, mundane management tasks. Network security policy management solutions offer automation and orchestration that allows your teams to focus their time on more strategic activities. By automating these tasks, you reduce the amount of money spent on them.
NSPM saves money and time with:
- Approval workflows that track and document change reviews and approvals that streamline change management processes
- Real-time tracking and notifications for change requests
- Audit trail documentation automation that reduces audit preparation time and costs
- Efficient troubleshooting for network and application connectivity issues with visibility into network topology
By centralizing and automation network security policy management with Tufin, your labor cost savings over three years can be up to $5 million just from the following efficiency improvements:
- 94% for network change analysis and implementation
- 85% for ongoing rule maintenance
- 95% for audit preparation and reporting
Digital transformation and application onboarding
Onboarding applications into your current network infrastructure can create various challenges. Your network administrators and application owners need to collaborate. Meanwhile, onboarding new applications can cause network-related application connectivity issues that lead to operational downtime.
An NSPM enables you to onboard applications more efficiently and cost effectively by:
- Streamlining application configuration with visibility into application connectivity dependencies
- Enabling collaboration with a central console for all network-related application connectivity changes
- Reducing downtime by proactively reviewing firewall security risks to prevent access issues
By automating configuration, processes, and audit documentation with Tufin, you improve your return on investment by deploying applications and establishing secure connectivity in minutes rather than days.
Tufin reduces application connectivity management efforts by 75%, with a labor efficiency over three years that can be valued at $715,000.
As your organization continues to onboard new applications to achieve digital business strategies, these cost reductions and improved return on application investments enhance your overarching bottom-line.
Onboarding and security policy propagation
A well-structured onboarding process means that new employees have faster access to the resources they need, enabling them to be productive sooner.
With NSPM, your network administrators and IT teams can more rapidly:
- Provide network access to new users
- Enforce user application and network access security controls
- Enforce acceptable use policies by setting security controls
Network simplification and performance benefits
Firewall optimization reduces your attack surface while improving overall network performance. When you have too many firewall rules, people struggle with connectivity speeds and application access.
Using an NSPM allows you to:
- Identify and troubleshoot unused, shadowed, or outdates rules
- Remove duplicate objects, like hosts or networks
- Automate the detection and decommissioning of expired and unused rules and objects
- Clean up your rules continuously to ensure a predictable network security posture
Regularly identifying and removing these unnecessary rules streamlines network management and improves firewall performance. To gain the full benefit of this process, Tufin’s automation enables network administrators and IT teams to automate many rule management and cleanup processes with:
- Best Practices Reports that identify duplicate objects
- Rule and Object Usage Reports that detect fully shadowed firewall rules
- Expired Rule Reports that identify expired firewall rules
- Automatic Policy Generator (APG) that detects rules that are too permissive
How does network security policy management improve cybersecurity?
A well-defined network security policy management system enables you to promote operational resilience in the context of complex cyber threats.
Efficient cybersecurity and data protection compliance
Compliance often feels like a necessary evil. Customers require assurance over your cybersecurity posture, and data protection laws increasingly levy larger fines for noncompliance. Simultaneously, the compliance process is time-consuming which makes it expensive.
NSPM reduces these burdens while improving your compliance posture with:
- Capabilities for creating network segments to meet network security requirements
- Visibility into network topology for understanding how sensitive data moves across networks
- Risk assessment workflows and automation to streamline the change management process
- Vulnerability identification, prioritization, and remediation to meet patch management requirements
- Reports and compliance mapping that auditors can use as documentation
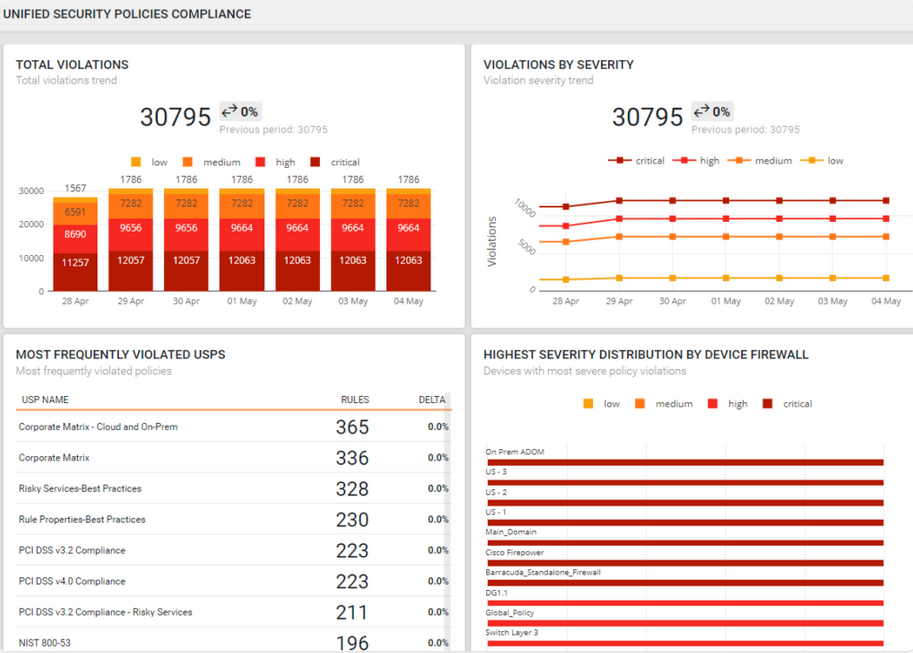
With centralized visibility in Tufin, you can automate time-consuming, error prone compliance tasks and gain centralized visibility with vendor-agnostic security policies. Additionally, ready-made templates configure policies so that they align with the industry regulations and standards that matter to your business.
Threat monitoring and incident response
Zero trust architectures are increasingly popular because malicious actors use credential-based attacks to gain unauthorized system and network access.
With a network security policy management solution, you can continuously monitor for threats and improve incident response processes by providing:
- Visibility into network topology to help trace suspicious activity across systems
- A centralized management console for reviewing firewall rules to identify misconfigurations that malicious actors could exploit
- Vendor-agnostic network security policies so that incident response teams can take real-time actions for isolating threats
- Security information and event management (SIEM) tool integrations to enhance security alerts and investigations with relevant firewall data
For example, with Tufin’s visibility into connectivity dependencies, security teams can more rapidly identify:
- Applications hosted on an impacted system
- Connectivity allowed to/from the hosts
- Insights into possible attack vectors or pivots made from hosts
- Potential lateral movements of threat actors
Cloud security
Your firewalls manage the communications to and between your on-premises data center and multi-cloud environments. Implementing secure configurations for application and network access is difficult but maintaining them is harder.
NSPM improves your overall cloud security by enforcing access controls by:
- Consolidating cloud-native and on-premises firewall management into a single console
- Managing on-premise or cloud-hosted firewall security policies the same way as SASE, SSE, and SD-WAN
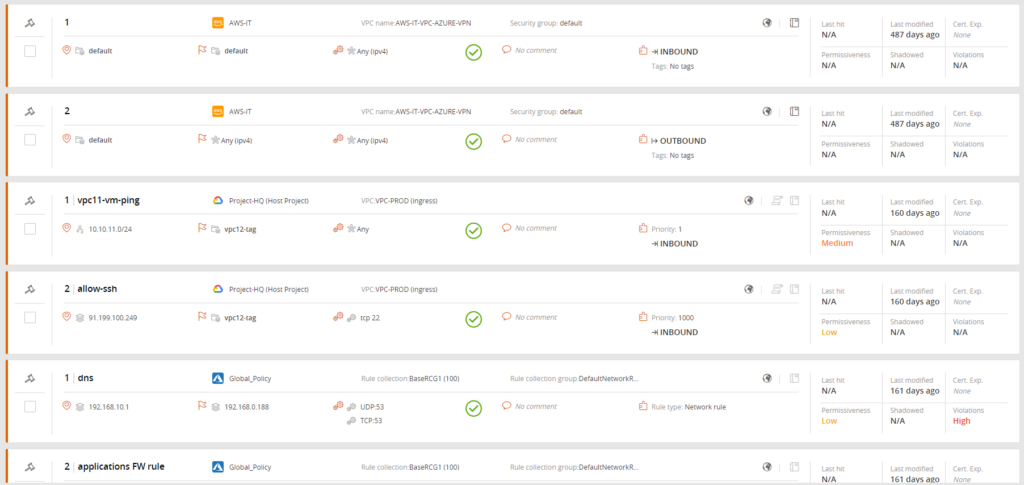
Managing assets, services, and traffic across multi-cloud environments with a centralized compliance management console reduces overall cloud security costs. For example, with Tufin, you can design, deploy, and automate network security policy management across AWS, Azure, and Google Cloud Platform in one place which reduces the time network administrators, IT teams, and security teams spend moving between different management tools.
Tufin: Improving Network Security While Reducing Costs
Tufin automates and streamlines network security policy management from a central dashboard so that your teams can collaborate more effectively and digitally transform your organization more securely. With our Unified Security Policies (USPs), you can create consistent rules across network devices that support continuous compliance monitoring. With this consistency and our network topology maps, you can go beyond implementation to focus on enforcement and optimization. Our security policy rule management and cleanup capabilities reduce your attack surface while improving network functionality, like a buy one get one free coupon.
To learn how Tufin enables cost effective security and operations outcomes, schedule a demo today.

Don't miss out on more Tufin blogs
Subscribe to our weekly blog digest











