Despite the continued acceleration of cloud adoption, recent research noted that 73% of organizations have hybrid network environments. Many organizations maintain both on-premise and cloud networks to balance data control and security with infrastructure costs and scalability. However, for network operations and security teams, these hybrid environments can create a morass of network security policy mess.
Hybrid environments often bring with them disparate network security tools. As your organization scales its cloud infrastructure, you can find yourself managing various tools, including technologies like:
- Traditional firewalls
- Next-Generation Firewalls (NGFW)
- SASE
- SD-WAN
Problematically, these diverse technologies lead to fragmented network security policies that exacerbate inconsistent policy enforcement across diverse network devices. To overcome the challenges that fragmented policies in hybrid environments create, you should consider solutions that provide vendor agnostic network security policies and automation that enable continuous compliance.
Understanding the Challenges of Fragmented Network Security Policies
In hybrid environments, the demand for scalability and flexibility inadvertently expands the attack surface, making the network more vulnerable to cyber threats.
Without uniform network security policies across the environment, organizations face challenges like:
- Policy drift where older rules remain unevaluated, expanding the attack surface
- Inability to regularly review and update routing tables and static routes
- Policy inconsistencies that create compliance violations which can lead to fines and penalties
- Failure to align business objectives with network access needs
Importance of Centralized Management for Network Security Policy Management
Centralized management is essential for cohesive, efficient security policy administration in hybrid environments. With integrated visibility and simplified policy enforcement, you can apply consistent network security policies across the disparate network infrastructures to improve security, compliance, and service availability.
Visibility
Integrated visibility into all network traffic is crucial for monitoring and controlling security policies. You need a single source of information to
- Monitor network security controls effectiveness
- Ensure that you limit access according to the principle of least privilege
- Maintain appropriate network segmentation for critical assets
A unified approach allows network administrators and network security professionals to quickly identify and mitigate risks, ensuring robust network protection.
Simplification
With a central location for all security policy management, you reduce the time spent looking through different vendor-supplied tools. By consolidating disparate security controls into a single dashboard, organizations can:
- Streamline policy creation, deployment, and management across multiple IT environments
- Respond to incidents faster
- Reduce human error risks associated with manual processes
Consistency
When you have comprehensive visibility into your network, you can identify areas of improvement by comparing access and permissions. As you work toward building a zero trust architecture, using a network security policy management’s automation means you can reduce the time spent managing diverse firewall enforcement points, such as cloud, virtual, and on-premises solutions.
Overcoming Security Policy Fragmentation
As organizations integrate diverse network devices and cloud platforms, maintaining consistent security policies becomes vital to managing potential threats and protecting your security posture. Addressing security policy fragmentation is essential to reduce attack surfaces and ensure seamless network connections.
Create Consistent Security Policies
Vendor agnostic policies unify visibility and control by consolidating security policies for various environments, including on-premises and multi-cloud environments. With visibility into diverse environments from a single location, you gain a clear, contextualized view of users, data, infrastructure, and potential threats, enhancing your security and compliance posture.
Tufin’s vendor-agnostic Unified Security Policies (USPs) allow you to simplify your network security policies so that you can more effectively maintain your desired network segmentation, even with a constant influx of change requests. Our USPs enable you to define the traffic you want to allow between your network zone so you can monitor it, measure it, and identify policy violations.
With vendor-agnostic USPs, you gain visibility into your network topology across different types of network environments, including on-premises data centers and cloud-based environments. Since you can visualize and handle all networks from a central hub of security truth, you can respond to incidents or compliance violations faster while maintaining service availability.

Implement Automation
By automating the application of security policy changes across diverse platforms and edge technologies, you can reduce operational overhead and minimize the risk of security gaps.
Automation allows you to focus on high-value tasks, like assessing and mitigating risk, rather than routine manual configurations. With risk-aware workflows, you can assess the impact changes have on your security posture prior to implementing them. Since the workflows document your change management processes, this improves your compliance posture and reduces overall audit costs.
Tufin’s network change automation streamlines processes and ensures continuous regulatory compliance. Our integrations with IT service management platforms and ticketing systems means that you can automate the change request process, with approval workflows that ensure the appropriate people review and approve changes prior to implementation.
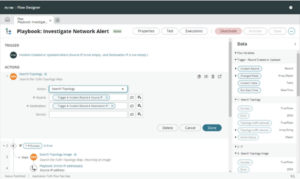
Tufin’s automation builds risk analysis and review into the workflows so you can achieve the following efficiency improvements:
- 95% for network change analysis and implementation
- 85% for ongoing rule maintenance
- 95% for audit preparation and reporting
Regularly Audit Firewall Rules
Your networks are dynamic, and a single change can have a cascading effect across your network security. These proactive assessments validate rules and reduce the number of unnecessary changes you make. For example, they can help you understand your network infrastructure and identify issues like:
- Misconfigurations and risky changes
- Modifications and deployment times
- Different firewall policy versions that can impact how intended changes affect your security
With Tufin’s platform, you can use an automated firewall audit checklist to discover issues and document change management processes for consistent monitoring across firewalls, routers, SDN, and hybrid networks. Using automation enables you to schedule real-time customized audit reports or run on-demand audits to address potential vulnerabilities. When you use our firewall audit tools, you can provide immediate verification of firewall compliance to prove conformance to internal controls and mission-critical regulations, frameworks, and standards, ultimately reducing audit preparation times.
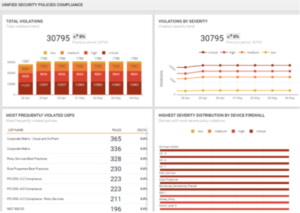
Optimize Rules
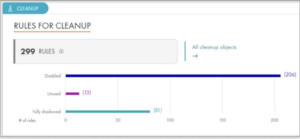
Optimizing firewall rules involves the removal of overly permissive, outdated, and shadow rules, effectively reducing the attack surface and improving network performance. Eliminating or reordering rulesets provides various benefits like:
- Improved network device performance
- Proactive vulnerability remediation
- Improved anomaly detection
- Faster response times
With Tufin, you can rapidly identify and troubleshoot unused, shadowed, or outdated rules to reduce your attack surface and improve network speeds. Aligning security policies more effectively with business objectives makes managing risk easier, especially when you can identify, review, and document reasons for maintaining low-use rules. Our platform automatically identifies and decommissions unused, shadowed, or outdated rules to streamline time-consuming processes.
By tightening overly permissive rules and consistently enforcing the principle of least privilege across network devices, you can control access more precisely. Our automatic policy generator (APG) reviews actual rule usage so you can identify and tighten these rules based on real user needs so you maintain availability while improving network security.
Continuously Monitor
As your organization adds new applications, you further expand your attack surface. With high volumes of new requests and access changes, you can easily experience policy drift. Continuous monitoring enables you to identify areas of improvement regularly, allowing you to create a resilient security posture that ensures continued uptime.
Tufin’s orchestration suite enables you to engage in real-time monitoring and alerts to security policy and regulatory compliance risks. You can continuously analyze and minimize your attack surface with a comprehensive view of your network, from a holistic view to a detailed breakdown of critical zones, exploitable rules, and exposed assets. As you iterate your network security processes and posture, you can compare your current exposure levels to past states, using trend-based insights to analyze how your efforts impact your total attack surface.
Tufin: Centralized, Consolidated Security Policy Management for Hybrid Environments
Using Tufin’s Orchestration Suite, you can consolidate all network security policy management into a single location across your on-premises and multi-cloud environment to unify security operations across network and cloud security teams. You can consolidate compliance across legacy firewalls, next-gen firewalls, SDN, SASE, and Edge devices using a central console for continuous regulatory adherence and internal policy enforcement.
To learn how Tufin can help you gain visibility, simplify security policy management, and consistently enforce security controls, contact us for a demo today.

Don't miss out on more Tufin blogs
Subscribe to our weekly blog digest










