I’m very proud to announce another innovative capability of the Tufin Orchestration Suite: automation of next-generation security policies on Palo Alto Networks firewalls.
What does this mean?
It basically means that security teams can automate the implementation of network flows across heterogeneous firewalls from Check Point, Cisco, Juniper and now, Palo Alto Networks too.
Here’s a typical scenario:
A network engineer needs to provide connectivity for a new application or service.
She accesses a web console and defines the required flows: servers, ports, services and… applications!
Next-Generation Firewalls improve security by allowing us to reach a fine level of control using application identities rather than the old-fashioned TCP and UDP ports. And the Tufin Orchestration Suite is the first platform to automate changes for Next-Generation Firewall flows – including applications.
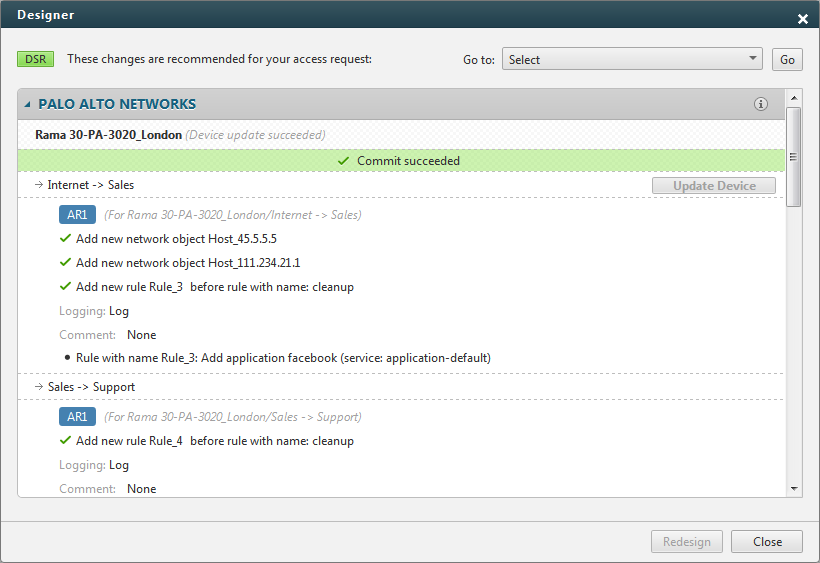
Next, the Orchestration Suite performs a risk analysis, discovers the relevant firewalls and network interfaces through a network topology analysis, and designs the optimal policy changes per firewall.
The security administrator can review the “cookbook” of recommended changes per firewall and click a button to commit or stage the changes.
Minutes later the change is fully implemented and automatically documented, and the new application or service is fully connected and ready to go live.
This type of automation goes beyond calling APIs to change a specific firewall – it is completely abstracted from the underlying network complexities and specific vendor implementation. Tufin can implement the right rules on the right firewalls with minimal user intervention (or none at all, if desired) yet we still offer full control and visibility.
Firewalls are here to stay and automation is the new rule of IT – combined you get the best IT agility and network security!
Ready to Learn More
Get a Demo





