Now Required: Rule Justification and Ownership
In an effort to promote electronic payment innovation while decreasing potential security risks the European Banking Authority (EBA) and the European Central Bank (ECB) published an Assessment Guide for the Security of Internet Payments[1]. Implementation is required by December 31, 2020[2]. This guide sets the minimum security requirements that EU Payment Service Providers (PSP) are obliged to implement.
ECB requires least privilege access. According to ECB guidelines, every creation or modification of an access rule must include documented justification for the connectivity, with business owner details and approval. Rules must be recertified every 180 days. To achieve least privilege access, only justified rules can be implemented. Financial institutions that cannot meet least privilege access and rule recertification requirements need to present a remediation plan to ensure that they can meet the guidelines in the near future.
While in theory least privilege, limiting access to only what is needed, sounds simple, implementation presents many challenges. Faced with increased network complexity and a growing number of applications and security policies spanning hybrid network environments, financial institutions can no longer rely on disparate solutions or manual processes to monitor and control network access privileges and maintain compliance.
Network Security Policy Automation: A Single Platform for All Requirements
An automated Network Security Policy Management (NSPM) system can provide a centralized solution for fulfilling all capabilities. With NSPM, security, network, and cloud operation teams can control and view real-time information. This entails full visibility and control of which apps, workloads , and network devices (e.g. SDNs, firewalls, routers, and switches) are currently deployed, and their security policies: how they’re connected, what can talk to what, and who can talk to who. A robust NSPM solution can span a complete multi-cloud, multi-vendor, hybrid environment.
Six Capabilities Needed for ECB Compliance
Least privilege access, documentation and recertification require six core set of capabilities.
Capability 1: Access Workflow Management.
Before an organization can embark on ECB compliance, it must have a defined and documented workflow for granting connectivity access. This workflow needs to be a repeatable process, with the ability for adherence to be monitored. Regulations further require separation of duties, whereby workflows must be defined such that, for example, an employee requesting access is not the same individual granting access. To learn more about Tufin’s suggested best practices and range of automated workflows, visit here.
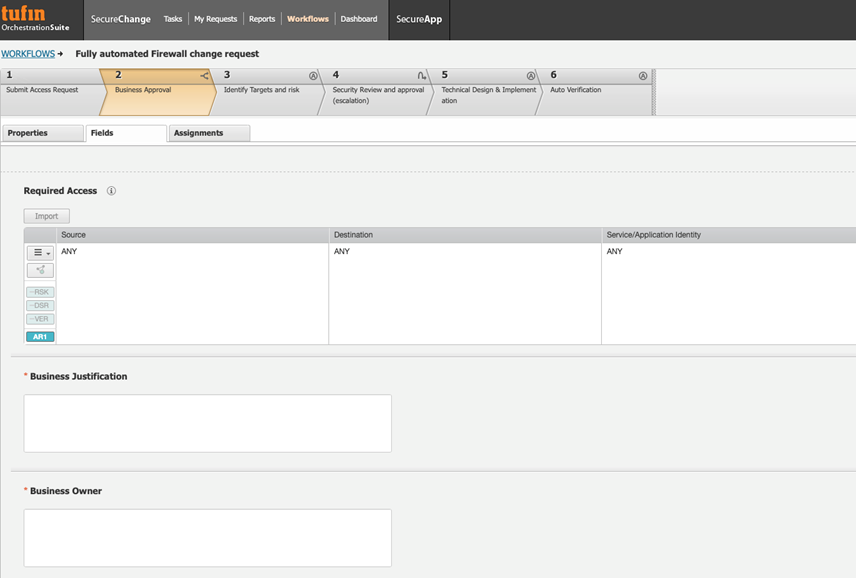
Screenshot showing the automated workflow an application access request undergoes including i. initiating the request, ii. business approval and justification, iii. path and risk evaluation, iv. risk review and approval if outside of standards, v. impleme
Capability 2. Continuous Application Discovery.
ECB regulations are based on an application-centric view, therefore, an up-to-date list of applications or workloads that require connectivity is required to ensure least privilege access.
Capability 3: Access Request Metadata.
All application connectivity requests must be backed by business justification and an owner. This requires the solution track not only the requests, but also justification and ownership of the requests as part of the change or access workflow. A means of collecting, tracking and associating the metadata with each rule must be established.
Capability 4: Linking the Application Access Requests to Security Policies.
In an audit, in order to prove that the access policies have business justification and an owner, the application-centric access requests must be able to be tied or mapped to the network security device or security group policies. A simplified view of what this mapping might entail, is illustrated below.
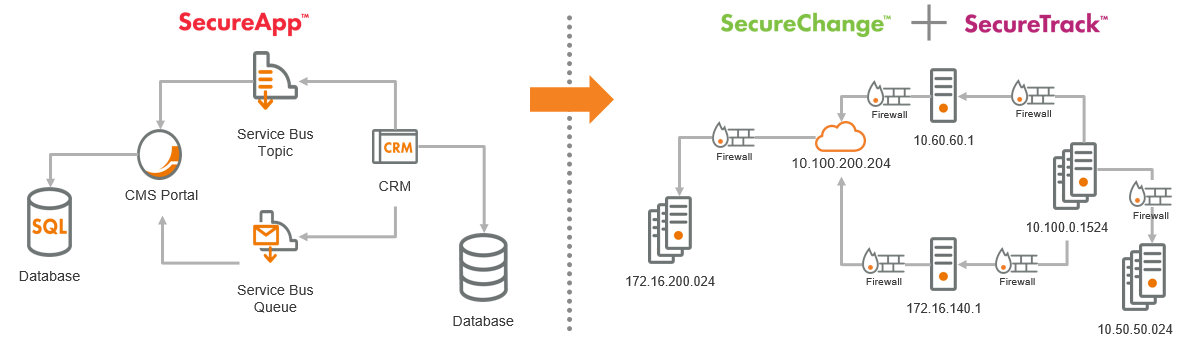
Left side shows an application-centric view of access requirements; while the right side represents the implementation or security device/group translation of the requirements
Capability 5: Adherence to Corporate Standards.
Security policies resulting from the access requests must comply with the organization’s standards. This requires a central repository of standards against which all policies are compared.
Capability 6: Tamper-proof Recertification.
Organizations must review the existing rule base and ensure each of the above measures are properly implemented on a regular basis. The guidelines do not specify the frequency, though it is generally agreed upon by public audit firms to be every 180 days. A comprehensive NSPM solution will provide a single, integrated platform that can meet all six capabilities. To keep up with network changes and manage continuous implementation and documentation organizations must leverage automation.
Tufin – A Complete Solution
Tufin’s network security policy management solution can help European financial institutions address ECB requirements. Tufin’s Orchestration Suite (TOS) provides end-to-end visibility of access or change requests, apps, communication paths, and network security devices and platforms, and an ability to achieve auditable and accurate network change management. With TOS you can ensure changes are documented and ECB compliant as well as consistently applied to any app or workload across your entire environment or platform. In addition to fulfilling ECB compliance, TOS provides increased efficiency, business agility, and reduced security risks. To learn more about how Tufin’s automation and orchestration of network security and firewall policies from a central console can help you reduce risk and ensure audit readiness for the next ECB audit, download this whitepaper today. References: 1. Originally published in February 2014, View PDF 2. Extended date from the original deadline
- Home
- Blog
- Regulations and Compliance
- Six Capabilities Required to Meet ECB Network Security Audit Requirements and Achieve Least Privilege Segmentation










