Firewall administrators are constantly dealing with frequent change requests that strain their resources, leaving little time for more pressing needs. This stress on the firewall team can have a negative impact on network performance and security. Often, when the choice is between quickly deploying a business-critical application or delaying deployment for the sake of security, the business wins out – significantly increasing risk for your organization.
The Challenges of Server Decommissioning
Server decommissioning is one example of a firewall task that because of its difficulty to execute, is mostly either ignored altogether or never fully completed. When a server comes to the end of its usefulness, it makes sense to remove it from the infrastructure in a controlled manner. Understanding all the implications of removing or migrating an old server using manual processes is complicated, and as a result, many organizations are scared to turn off their old servers for fear of breaking something.
Complications introduced by obsolete servers that are not properly decommissioned include:
- Increased vulnerability from old software and operating systems that may no longer be supported or have patches available
- Poor performance and increased risk due to duplicate IP addresses
- Interrupted business continuity caused by unaccounted for, dependent applications
- Delays in problem resolution because of inaccuracies in the IT documentation
To avoid these pitfalls, an automated approach to server decommissioning is needed. To see if you are a candidate for an automation ask your organization the following questions:
- How long does it take to decommission a server?
- What resources are required and how often is it performed?
- Are there technical or procedural dependencies that slow down the change process?
- What is the opportunity cost of your firewall admins spending time on manual tasks?
- Are you slowing down your network by not optimizing connections?
Chances are that you need automated server decommissioning.
Best Practices for Automated Server Decommissioning
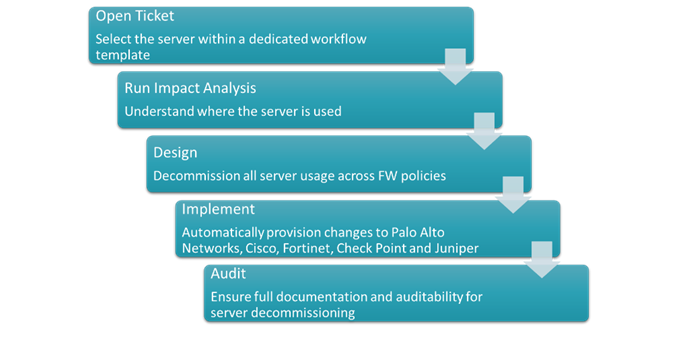
To build an effective server decommissioning process, establish a repeatable workflow with well-defined steps. Begin by identifying the targeted server, then:
- Open a ticket
- Run network impact analysis
- Design rule change
- Implement rule changes
- Document and audit the entire process
An impact analysis run across the entire network is a critical step in this process for you to understand the full effects that removing the server will have on the network and other applications. Depending on how large your organization is, this analysis can become very complex — very fast, requiring a solution that identifies all server dependencies automatically.
Automation of the server decommissioning process offers a clear view into all instances of the server in every policy and device and provides guidance for the server’s removal. To have full control over the process, it’s essential to have a choice between using fully- or semi-automated decommissioning when you design, implement, and provision the server removal.
Any automated process must help you capture why the change was made, who made the change, and when, to meet internal and external audit and compliance regulations after the server is decommissioned.
Automate for Greater Efficiency and Reduced Risk
To improve the agility of your enterprise, automation is critical to provide greater visibility and increased efficiency to meet compliance mandates, improve network performance, and reduce risk. Automation is a journey that begins with firewall tasks, like server decommissioning. Contact Tufin to learn more.
FAQs
What are the best practices for decommissioning a server?
Establish a repeatable workflow with well-defined steps. Begin by identifying the targeted server, then open a ticket, run network impact analysis, design rule change, implement rule changes, and document and audit the entire process.
- Home
- Blog
- Firewall Best Practices
- Firewall Best Practices: Decommissioning a Server










