Today’s massive hybrid networks are a result of an eclectic mix of new and old technologies. As apps, workloads, and now, users move outside of the perimeter, the heterogeneity and complexity of our IT environments continues to expand. The result is a wider scope of tools, operations, and knowledge required by network admin and security teams. There are now dozens, if not hundreds of firewall or firewall-like solutions that organizations need to manage across their heterogeneous infrastructure. As the multi-tiered approach to protecting organizations’ critical data and applications continues to grow, there is no end in sight to the expansion.
A typical application architecture illustrates the network complexity that network and security teams are navigating. This typical application is likely spread across several cloud platforms with some workloads running in public clouds, and others, in private clouds. Some elements are likely operating on a virtual machine, while other are operating in a Kubernetes-managed environment. Many, if not most of these parts require access to an on-premises data source. Meanwhile, authentication is performed using an external service. And then of course, users connect via the internet. One thing we know to be true — security policies need to be managed across the entire environment. It’s here that the importance of unified network policy management demonstrates its relevance.
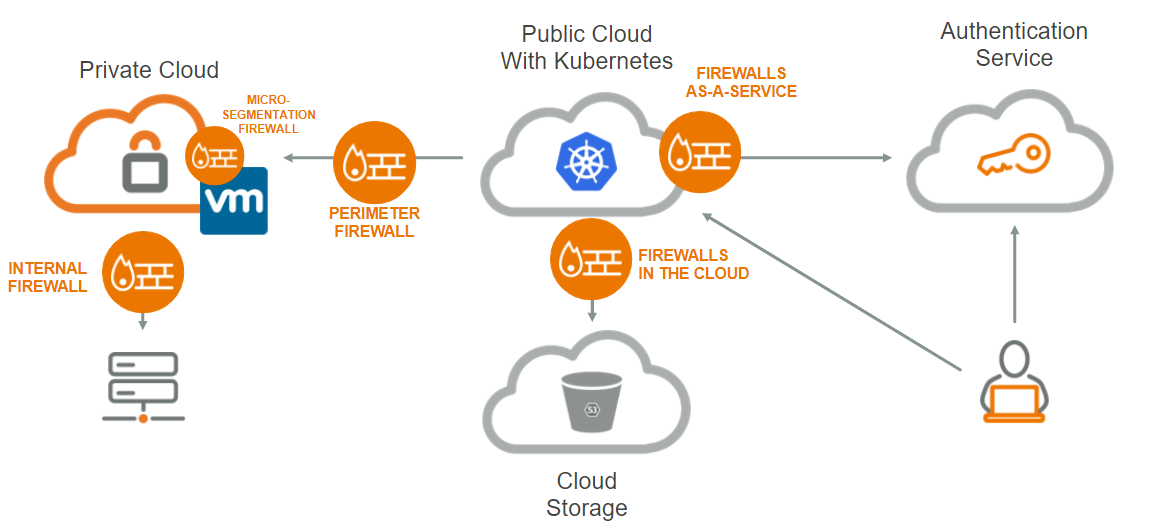
A typical application architecture demonstrating over 5 sets of security policies that need to be managed to enable the application.
Today’s Firewalls have Many Different Names

Based on a broad firewall definition of any device or software that enforces a policy of who can talk to who or what can talk to what, the “firewalls” that large organizations use today to manage various types of segmentation, could include:
- Perimeter or internal firewalls including Next-Gen Firewalls, providing N-S connectivity to/between VPCs or VNets
- “Firewalls” that manage E-W access: such as Security Groups in the cloud and Network Policies in Kubernetes
- Firewalls as a service in the cloud
- IAM and RBAC: essentially identity “firewalls” managing identity access policies
- Authentication services- a form of identity firewalls, as they determine which users can access which aspects of the application
- Operating system level “firewalls”- provide isolation between applications and the OS level
- Application level firewalls – proxies, load balancers and application gateways
- Web application firewalls – WAF

The generalized concept of a firewall demonstrates the technologies and scopes of policies involved. Not only are the number and types of “firewalls” growing, but as more and more functionality gets folded into them, administration requires additional skills, better network visibility, and a deeper understanding of the applications’ business logic.

The Benefits of Automation
Centralized control and visibility of all of these policies, coupled with automation, is the only viable solution that is sufficiently scalable and secure to handle this growing complexity. Configuring each category of “firewall” manually is time consuming and inefficient, and can lead to a lack of consistency, leaving blind spots and weakening a security posture. With the multitude of moving parts, misconfigurations are bound to take place. With a centralized security policy console that provides visibility into this range of “firewall” policies, policy enforcement can be harmonized across the entire network.
Extract Policy from the Implementation
Beyond multi-vendor control and automation, the future of policy management lies in abstraction. Just as object-oriented programming separated data and code, extracting the policy “code” from the infrastructure will allow for increased flexibility and more comprehensive management. As networks are not static, as the heterogeneity will grow and implementations will change, admins need to extract policy away from implementations. They need unified and central management to control who can talk to who and what can talk to what, that maintains its relevance as the underlying IPs, security groups or platforms change. This will in turn, provide the much-needed flexibility and consistent policy management and enforcement, with in-depth, unified visibility of the entire network.
Your security is only as good as your policy – firewalls need to be configured to adhere to the least-privilege principle at all times.

Interested in Learning More?
Listen to Tufin CTO & Co-Founder, Reuven Harrison, as he provides more detail on the growth of security policies across today’s IT environments, and techniques for comprehensive and consistent management of these policies.
- Home
- Blog
- Firewall Best Practices
- To Have or Not to Have: Firewall Policies as Part of Your Security Strategy