Picture the scene. You decide to take your 3-year-old to the theme park for a fun day out. You buckle her into the child seat (you chose for its safety standards) in the back seat of your car (also chosen for its safety standards). You drive carefully all the way to the theme park, and upon arrival, you let her walk through the gates and wave as she heads off on her own to whatever ride or distraction has her attention.
There are no adults to look after her and now that you’ve lost sight of her on the other side of the gate, you realize you have no idea what dangers exist on the other side—are there other ways out of the park? Unseen perils? And what about the fun-house mirrors to make things look like something they aren’t? You have no idea what is in there, yet you are expected to walk away and assume the best. Would this be acceptable to you?
This is exactly the scenario we are seeing with public cloud. Organizations are being told they can protect their cloud environment with a perimeter firewall and security group configuration. But, beyond here, there is no visibility. No view of the many misconfigurations in the cloud. Incorrectly secured buckets, insecure ports in use, overly permissive networks… We call this Inter-VPC security. You’ve secured the perimeter of your virtual private cloud.
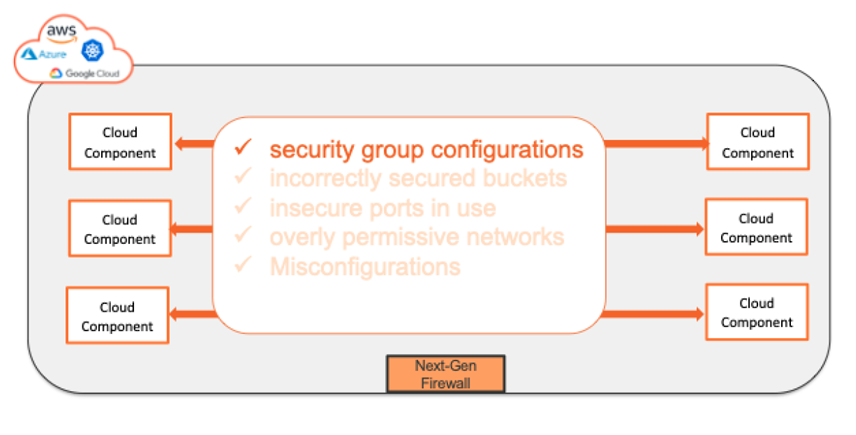
But,what if you want to truly secure everything inside and outside your cloud? (Of course, you want to keep your 3-year-old safe wherever she goes.) To start, you must have visibility of what is happening. The old adage says you cannot protect what you cannot see. You must understand what is talking to what and who is talking to whom.
The latest information from CISA is that most malicious actors are gaining access to your cloud environments though phishing attacks due to poor cyber hygiene and by leveraging egress and ingress traffic flows to gain access to sensitive data. This completely bypasses your perimeter defenses and allows bad actors to crawl the network looking to elevate their privileges and ultimately exfiltrate data. This issue is further compounded by the speed of change in cloud environments. Typical firewall changes require an approval process that is often manual and involves multiple layers of authorization with various people responsible at different levels—network, cloud, operations, security, etc. This all means that you’ve lost much of the speed and agility promised by the cloud. Without a means to automate against an agreed-upon set of security policies, the toll on resources can only slow down critical firewall changes.
This is only part of the story. Using legacy security methodologies to secure a highly agile cloud environment also increases the cost of using the cloud as additional skills are required. These costs come with the investment in personnel or training to secure the cloud or the time required to work within multiple tools. For some organizations, vendor lock-in becomes a reality as they are forced to take the path of least resistance.
In order to combat these very real threats, organizations need the trinity of security: visibility, guardrails and action. Visibility to see what is talking to what and who is talking to whom within the cloud. Guardrails to set and alert against violations. Action to implement the changes required to reduce the risks caused by misconfigurations and a lack of visibility. This trinity is essentially the security guard that will ensure your 3-year-old—or applications, data, and more—are secure wherever they go.
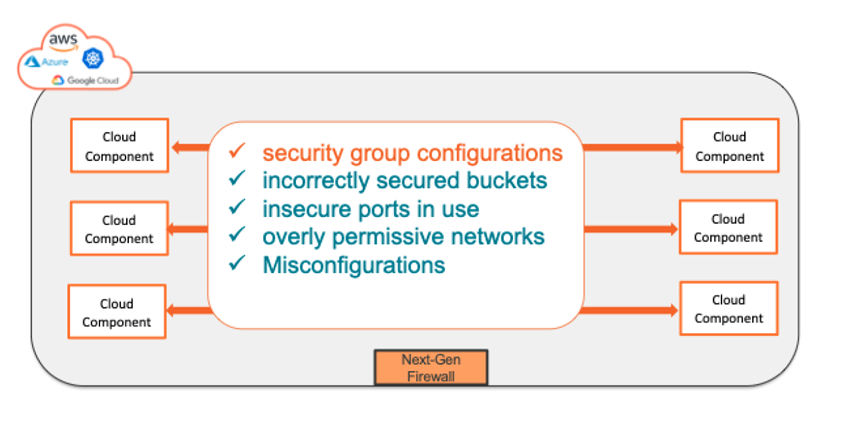
Security should extend inside your cloud as well as around the perimeter
This is Intra-VPC security. With this understanding across hybrid or multi-cloud deployments, you can truly start to implement security with the knowledge you are doing more than simply relying on perimeter defense. So, which type of security will you choose? Inter-VPC to protect the perimeter or Intra-VPC to ensure all elements of your cloud are secure, inside and out? The fact is, both are required to ensure the security of your hybrid cloud. Want to gain an visibility inside your intra-VPC? Get your free no-obligation cloud security assessment.
- Home
- Blog
- Cloud Security
- Inter-VPC vs Intra-VPC – Which One are You Securing?










