“Is it hard?’ Not if you have the right attitudes. It’s having the right attitude that’s hard.” (Robert M. Pirsig, Zen and the Art of Motorcycle Maintenance: An Inquiry into Values)
Network segmentation should be applied throughout the entire enterprise to ensure security. And we all know it. But like so many others of life’s ‘necessary but ultimately time consuming’ tasks, we just do the basics. Often this means little or no access to the internal network from externally facing networks; and a separation of control systems from the corporate sensitive networks – and we stop there. The problem is that’s just the start. So why don’t we do more?
According to Mark Wolfgang (President of Shorebreak Security), organizations don’t segment for security properly for two main reasons:
- They don’t understand their organization’s business drivers
- They don’t understand how an attacker operates.
A corner stone of security management, network segmentation limits the lateral movement of an attacker within the network and therefore reduces the overall impact of a security breach.
As Wolfgang puts it, understanding your organization is the first and most important step in segmenting a network. This means understanding the business drivers, the key IT assets, personal and data, and where these are located, how the organization makes money and what are the business processes that support it. It’s only once you define groups of assets and personnel that can you really consider placing them into different network segments. From there you need to define how the different network segments interact with each other and create sets of rules and restrictions to access the data.
Prioritizing the different network segments, based on the assets and risks associated with a compromise of that network segment is also crucial. This helps to effectively plan the implementation of the network segmentation. And also helps protect businesses from external threats.
In terms of the attack vectors, it is important to understand what an attacker is trying to get. The objective of an attacker is simple – to gain access to desired assets – whether that be system, data or person. They can go about this in a numbers of ways. They can try to attack the desired access directly; they can attack the network infrastructure or attack the people (or systems) who have access to the desired target. Whatever their goal is, an attacker won’t generally stop until it’s achieved. Unfortunately this often means that to reach a desired system, they will seek out and compromise different assets that have access to that system, via an indirect attack.
This is where network segmentation comes into play. Proper network segmentation helps block the path the attacker can take to access your assets. Most organizations who have done the segmentation exercise end up with spread-sheet mapping the different network segments and the relationship (or access restrictions) between them. Sadly, this exercise ends there, and over time this spread-sheet mapping becomes incorrect and out-of-date.
So I’d like to add a third reason for the generally inadequate segmentation of business networks to Mark’s two: the sheer scale of the task at hand.
What’s required is an automated approach to network segmentation, which helps organizations deal with their network segmentation far more effectively, in less time and without complication. Security admins must be able to visualize their network segments, define the access allowed between different segments and decide the priority for this access.
We’ve developed our security zone matrix to achieve just that. You start by defining the different network zones. Next you clarify the access allowed between the different zones and its priority, building a visual mapping of your desired network segmentation as you go.
You can then run an analysis to map the gaps between the actual segmentation (as enforced in your firewall rules and routers’ ACLs) and the desired segmentation; providing the security administrator with:
- a clear view of the gaps between his desired network segmentation
- priorities of changes that need to be made in order to comply with this network segmentation
- and a cook-book instruction set on how to fix the different security policies and router’s configuration in order to reach the desired network segmentation.
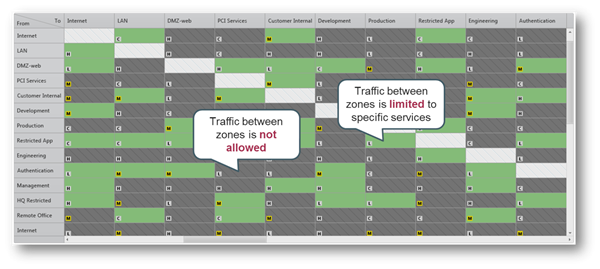
Tufin’s Unified Security Policy helps security administrators get great visibility to their network segmentation and stay on top of their segmentation in an ever changing and increasingly complex network landscape.
To paraphrase the words of Robert M. Pirsig, network segmentation should not be hard with the right set of tools.
Ready to Learn More
Get a Demo