One of the challenges when setting a new security rule or enabling connectivity is ensuring that access is not being granted to vulnerabilities. With the release of the Vulnerability-based Change Automation (VCA) App Tufin customers can automatically address this problem by integrating assessments into their existing processes or workflows.
The VCA automatically retrieves scan data from an organization’s vulnerability scanner and reflects the results in the risk assessment step of an access request workflow. Integration is supported with leading vulnerability management solutions including Tenable, Rapid7, Nessus and Qualys. Customers can proactively ensure there are no risky vulnerabilities in the source or destination of assets before provisioning new network access.
How it Works
With the VCA activated an additional security assessment is added to the SecureChange access workflow. Every time a new access request ticket is created or received in SecureChange (from an ITSM, such as ServiceNow) the VCA automatically sends the source and destination data to the external vulnerability scanner, and the historical results are immediately posted on the SecureChange risk assessment tab or a new active scan is scheduled. Based on the severity threshold a customer defines, and Tufin’s Unified Security Policy violation check, Tufin’s Risk Analysis Engine calculates the combined risk status, and helps determine if the access should be approved or sent to an exception process with the ability to fully automate the approval or routing to security, with included reporting.
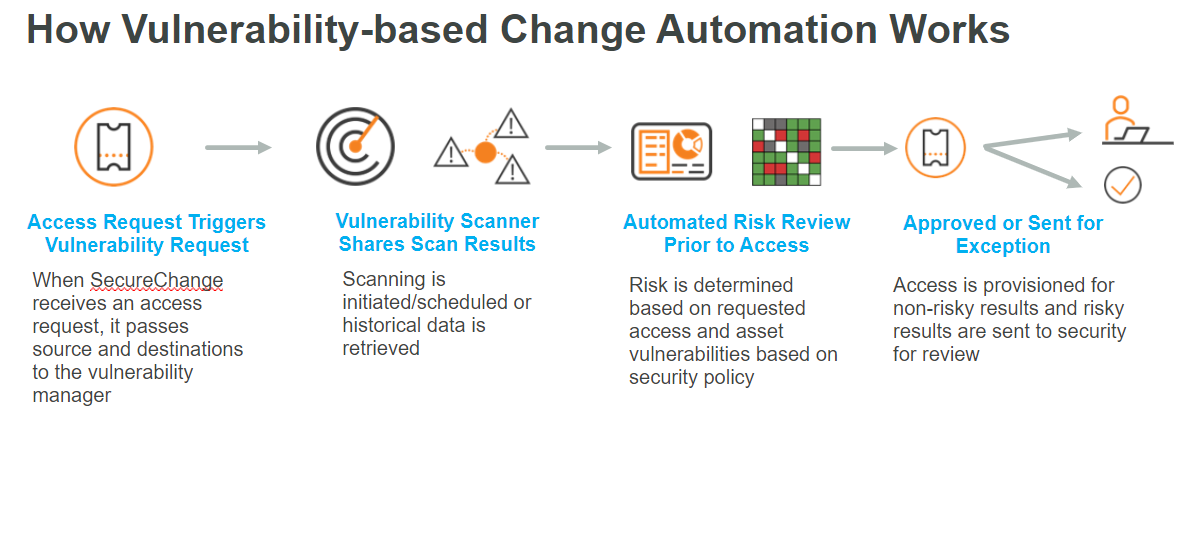
Integrating vulnerability scan data into automated provisioning workflows improves IT admin and security team’s ability to make better informed decisions, increasing the speed for network teams to implement secure changes. If the status is deemed high-risk the ticket can be escalated to an additional approval step by the security team, fostering collaboration across teams. The majority of access requests can be processed automatically, without any human intervention, allowing the team to optimize their time and focus on requests that contain a high risk and require additional review. The addition of the VCA allows IT and security teams to proactively identify security issues and prevent enabling access to vulnerabilities through automation, rather than play catch-up with time-consuming inspections and manual change implementation. For those not familiar with Tufin SecureChange, it’s a great tool to build, or alternatively use OOTB, workflows to automate common security policy management tasks. It increases efficiency, helps remove bottlenecks, and eliminates the risk of configuration errors in your daily operations. All workflows are audit ready, as they track and document the full change history, and store it for future reference.
See How Easy Vulnerability Management Can Be
VCA + Vulnerability Mitigation App (VMA)
The VCA pairs well with the Tufin VMA. The VMA integrates Tufin’s security rule base and network configuration knowledge with vulnerability data to identify vulnerable assets, that are accessible. The VMA enables organizations to prioritize remediation efforts and automatically apply mitigating controls by limiting access to assets with vulnerabilities. By combining vulnerability measures with insights into how these vulnerabilities may be accessed and exploited, customers have the context to identify and address vulnerabilities that pose the greatest threat to critical business assets, and mitigate or remove existing access, as required.
Combined Tufin VCA and VMA enable a context-aware and actionable vulnerability program
See the Tufin Marketplace to download both apps today.
- Home
- Blog
- Network Security Automation
- Tufin Expands Vulnerability Management With Automated Vulnerability Checks Prior to Approving a New Security Policy