It’s now the 17th year of the National Cybersecurity Awareness Month (NCSAM), making it the perfect time to announce the new release of Tufin Orchestration Suite (TOS) R20-2. This release delivers numerous new features and enhancements, such as considering additional risk assessment data, beyond information generated from Tufin’s Unified Security Policy, via third-party data input before provisioning new access, new capabilities to support your Next Gen firewalls, and enhanced visibility and traffic analysis for Azure environments.
Avoid risky access changes by integrating third-party risk assessment data
One of the key challenges when enabling a new access, a throwback to the very start of the pandemic, is to ensure that your source/destination is not vulnerable.
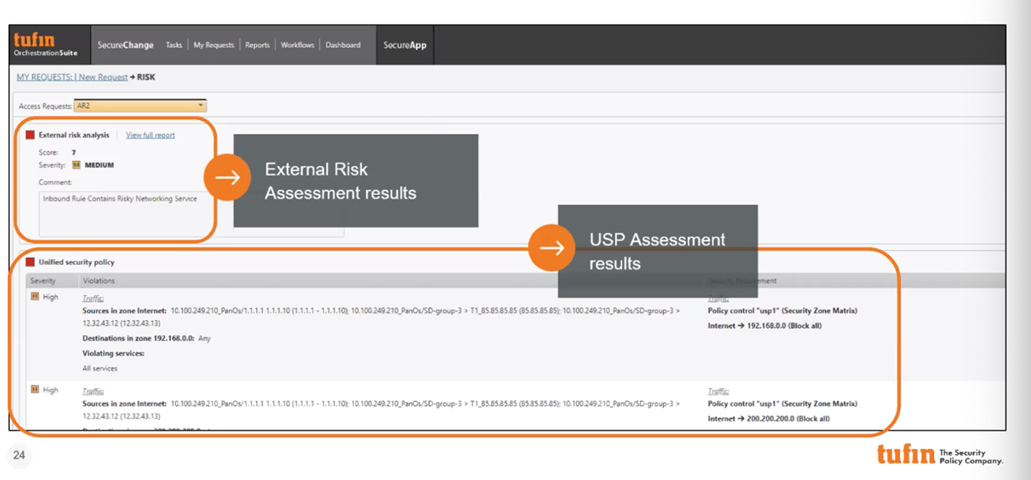
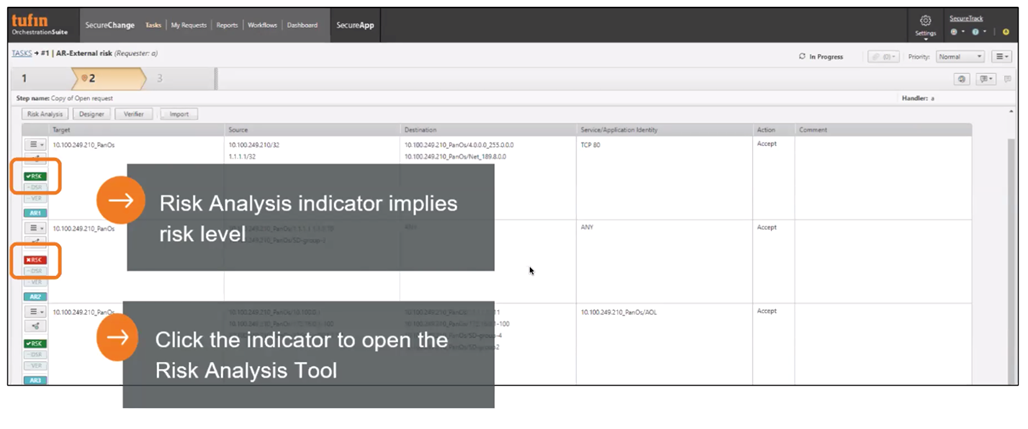
With R20-2, we doubled up the risk assessment step, so that in addition to assessing compliance to your Unified Security Policy, you can also quickly retrieve risk assessment data from a third-party tool (e.g. vulnerability management solution, SIEM, SOAR, or your endpoint security solution) into the Risk Assessment step in your Tufin SecureChange Access Request workflow. This way, you can proactively retrieve the results of additional security checks (e.g. vulnerability scores, risk severity) on the source/destination before provisioning new network access.
Once the additional security assessment is added to the workflow, every time a new access request ticket is created or received in SecureChange from your ticketing system (e.g. ServiceNow, Remedy or any other ITSM), Tufin automatically sends the source /destination data to the external tool, and the security check results are immediately posted on the SecureChange risk assessment tab. Based on the risk score, severity, and Tufin’s Unified Security Policy violation check, Tufin calculates the request’s combined risk status, to help you determine if to continue and implement the change.
Having this information available in a single SecureChange tab makes it easier for IT admins/security teams to make better-informed decisions whether to approve or deny the access, making it significantly faster for network teams to implement the change. The combined risk status can also help you fully automate the access request process: if the status is “no risk” or “low risk” – enabling Tufin to design and provision the change automatically. If the status is deemed “high risk,” can the ticket be escalated to an additional approval step by the security admin. This way, you can process the majority of access requests automatically, without any human intervention, and allow the team focus on requests that contain a high risk and require additional review.
If you’re not familiar with Tufin SecureChange, it’s a great tool you can use to build (or alternatively, use Tufin’s canned workflows) an unlimited number of workflows, and an easy, convenient way to help you automate your entire network change implementation process. With SecureChange, every workflow is a multi-step, graphical process – from opening a new ticket, to automated target selection, to risk assessment, approval, and all the way to network change design, implementation and verification. Simply put, it helps remove bottlenecks in your daily operations, and eliminate the risk of configuration errors. All workflows are audit-ready, as they track and document the full change history, and store it for future reference.
By using Tufin SecureChange workflows, your IT teams can proactively address security issues and network changes using automated processes, rather than ‘play catch’ with time consuming security checks and manual change implementation.
In addition to using external risk assessment tools for risk prevention, with Tufin, you can also use vulnerability scanner outputs for risk mitigation. Tufin Vulnerability Mitigation app is another newly-added solution we recently launched, whereby we integrate Tufin’s rule base information with leading vulnerability management solutions, such as Tenable, Rapid7, and Qualys. The Vulnerability Mitigation app enables you to prioritize remediation and mitigation efforts by enhancing vulnerability scanner output with network insights. By combining vulnerability measures (CVSS and severity) with insights into how these vulnerabilities may be accessed and exploited via the network, you’ll now have the context to identify and address vulnerabilities that pose the greatest threat to critical business assets, and mitigate or remove existing access, as required.
Extensive Next Generation Firewall Support for Palo Alto Networks (PAN) and Fortinet
As the leading vendor providing Next Generation Firewall (NGFW) support, in R20-2, Tufin has extended its support to now include the following features:
Palo Alto Network (PAN) NGFW – Panorama tag support
- Assign existing Panorama tags to new rules directly from Tufin – As part of the access change automation workflows, users can now easily assign tags to new rules directly from Tufin SecureChange, to help you better organize your rule base, and maintain uniformity.
- Automate access changes with custom applications directly from Tufin SecureChange – Users can now apply granular policies and automatically manage access changes for custom applications, providing full visibility, reporting, and control of all traffic for any app type (custom/predefined) on your network.
To learn more about Tufin’s Panorama NGFW support, click here
Fortinet NGFW support
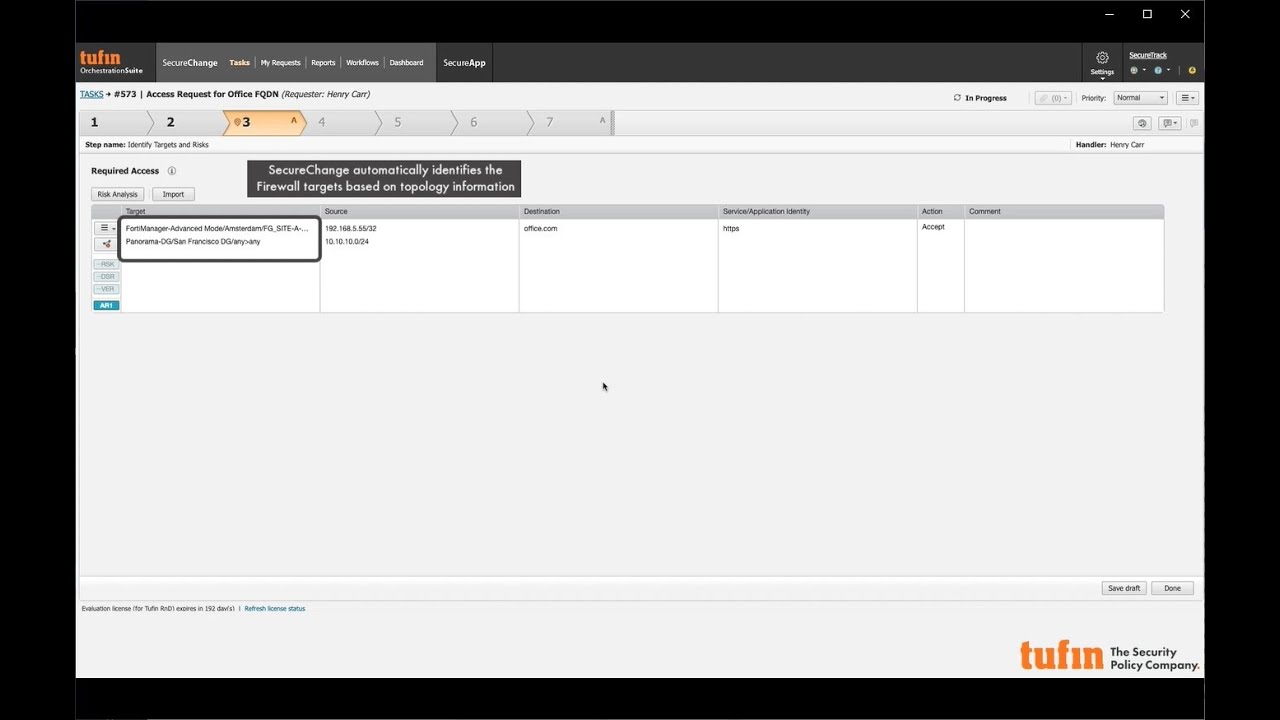
- Visibility and change automation for rules containing FQDNs – In R20-2, we’ve added the option to automate rule changes with FQDN objects. Now, you can optimize rules, implement new access or decommission rules with FQDN objects, all via your SecureChange workflows. In addition, you can use Tufin SecureTrack to view, search and track changes in FQDN objects, and detect misconfigurations, such as rule permissiveness, shadowing, etc.
- With R20-2, we deliver the same high level of support already provided for Palo Alto Networks FQDN in an earlier Tufin release. This is in keeping with our company’s mission — to enable you to successfully configure security segmentation policies and automatically implement changes, irrespective of the underlying platform, network security device, or objects used.
- In the video below, you can view how a new access change was implemented in a rule with FQDN object and applied to both Panorama and FortiManager.
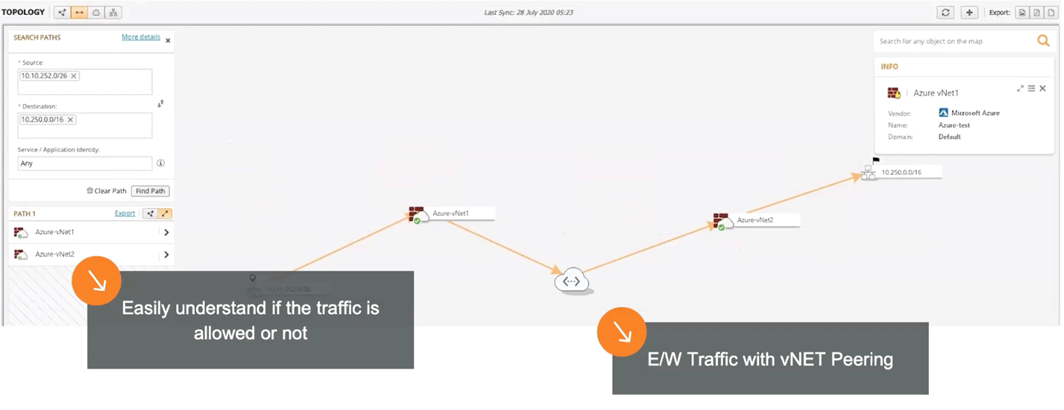
- Fast IPv6 path analysis and automated troubleshooting — You can now use Tufin SecureTrack topology intelligence to run IPv6 path analysis to display any relevant security rules in the path, and highlight whether any Fortinet firewalls are allowing/blocking traffic along the simulated path. Via the interactive topology map, you can also quickly plan changes, perform what-if traffic queries, or troubleshoot connectivity issues.
Enhanced visibility into Azure Virtual Network (VNet) traffic and beyond
As many of our customers use Azure, we provide end-to-end visibility and topology analysis, into north-south traffic between the on-premise environment and the VNet, and between VNets. There are multiple options to connect your on-premise environment to your Azure environment. With this release, we support the four most common connection configuration options – ExpressRoute, VNet Peering, IPSEC VPN, and third-party firewalls, allowing you to run traffic simulation query, analysis, and troubleshoot connectivity issues based on an accurate topology map. This will enable you to gain better visibility, to start efficiently managing and controlling your multi-vendor, fragmented network as one.
As with every new release, we work hard to onboard the newest innovations out there, improve ease-of-use, and deliver greater integration and support for additional security and network solutions, At Tufin, our aim is clear — to help enhance visibility and control across your multi-vendor, hybrid network. If you’d like to see a short Tufin R20-2 demo, contact us.
- Home
- Blog
- Cybersecurity
- What’s Inside Tufin R20-2: Enhanced NGFW Support, Azure Visibility, and Doubled Risk Analysis