For over 15 years protecting some of world’s largest and most complex hybrid networks, we at Tufin have a special appreciation of how a given network configuration impacts an organization’s overall security posture. Today, we announced that we are combining this insight with the results of vulnerability scans to enable users to improve their security posture. By looking at vulnerability severity and CVSS scores through the lens of network access to critical assets, security teams can effectively prioritize remediation efforts, and successfully mitigate risk – and that’s where Tufin’s new Vulnerability Mitigation app can help.
Risk-based Remediation & Mitigation
The challenge with vulnerability scans has always been too many critical vulnerabilities are discovered and not enough resources are available to patch them. Organizations need a way to prioritize the vulnerabilities that should be patched first and find a way to mitigate the risk from other vulnerabilities until they can be fully addressed.
Tufin Vulnerability Mitigation app, integrated with leading vulnerability management solutions, including Tenable.io, Tenable.sc, Qualys VMDR, Rapid7 Nexpose, and Rapid7 InsightVM, provides risk-based network insights to help organizations efficiently prioritize remediation and mitigation efforts by enhancing vulnerability data with network insights. By combining vulnerability measures (severity and CVSS scores) with insights into how these vulnerabilities may be accessed and exploited via your network, admins have the context to identify and address vulnerabilities that pose the greatest threat to critical business assets.
The reality is that vulnerabilities with high CVSS scores aren’t necessarily the ones being exploited. For example, a medium-level vulnerability associated with a business asset having multiple access points may be used by an attacker to penetrate your network and move laterally through your network to access other high-value, sensitive assets. As a result, this vulnerability is more prone to exploit by attackers, and consequently, should be considered a high-level priority for remediation or mitigation.
How the Tufin Vulnerability Mitigation App Mitigates Risk
Once installed, the Tufin Vulnerability Mitigation app retrieves vulnerability scan results and displays them in Tufin’s vulnerability dashboard. To save you time and effort, and identify the riskiest vulnerabilities to your business, you can choose to start with high-value network segments first, the same segments/zones that you defined in Tufin SecureTrack.
For MSSPs or large organizations using more than one vulnerability management solution, you can consolidate multi-vendor scan results – all from a single dashboard.
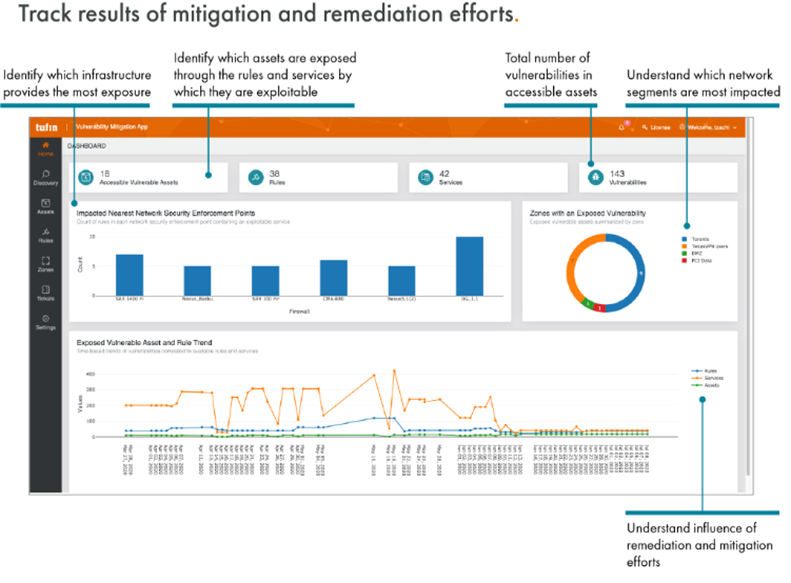
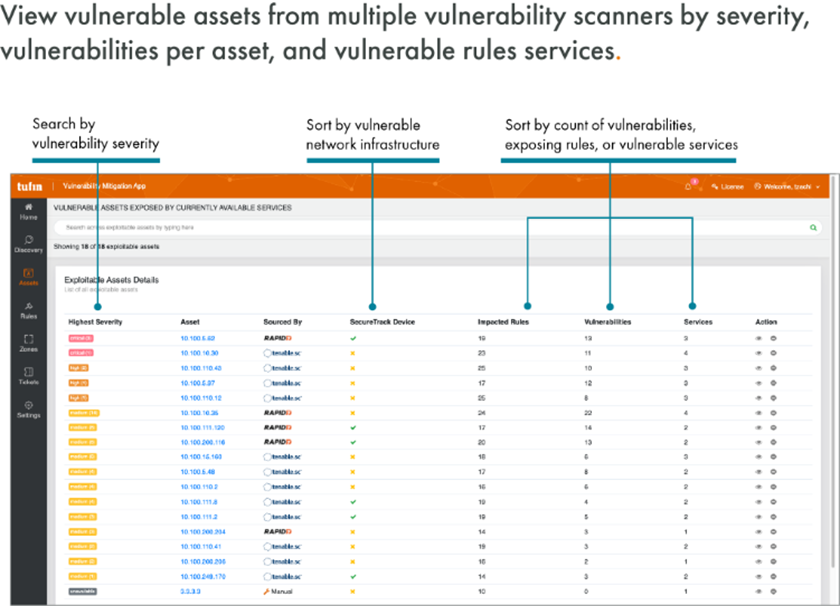
The Tufin Vulnerability Mitigation app lets you view a list of exposed vulnerable assets within the specified network segments and their vulnerability severity levels. You can also view the rules that govern access to and from a vulnerable asset, the underlying services exposing the vulnerabilities, and relevant firewalls that provide access. Through the vulnerability dashboard, you can track remediation and mitigation trends over time to help determine how your efforts are reducing your attack surface.
Prevent Vulnerability Exploitation Well Beyond a Patch
There are scenarios where patching is not always an option. For example, a patch may not be available or, if available, performing a patch may require costly downtime. And yet, your security standards and regulations may prevent use of the affected applications until known high-risk vulnerabilities are resolved. Tufin offers a process that can help address these situations.
Mitigate by Removing Access: Using Tufin’s Vulnerability Mitigation app, you can remove all network access associated with the vulnerable asset through Tufin’s pre-configured server decommissioning workflow, an automated process initiated directly from the app.
Tufin SecureChange then streamlines the network change implementation process to locate and update all rules enabling access to this vulnerable asset in all relevant network security devices and infrastructure components, such as firewalls, SDNs, routers, and security groups across the hybrid environment. The necessary rule changes are designed and implemented, automatically removing access to the vulnerable asset. Tufin then validates that the change was implemented as intended. It’s a fully automated and tracked process that can be managed directly from the app, as well as integrated with your ITSM solution workflows. Through this process, the Tufin Vulnerability app allows you to mitigate the risk of unpatched vulnerabilities that put your high-value assets at risk.
30-day Free Trial
Tufin Vulnerability Mitigation app is available to Tufin customers for a free 30-day trial and can be downloaded from the Tufin Marketplace, which offers apps that help users enhance protection, enable faster detection and deliver intelligent responses across a wide range of security and IT domains.
To download the Tufin Vulnerability Mitigation app for free 30 day trial, click here.
Ready to Learn More
Get a Demo