The industry’s leading network topology mapper makes Tufin one of the most powerful and accurate network monitoring solutions, providing real-time policy violation alerts and security posture awareness.
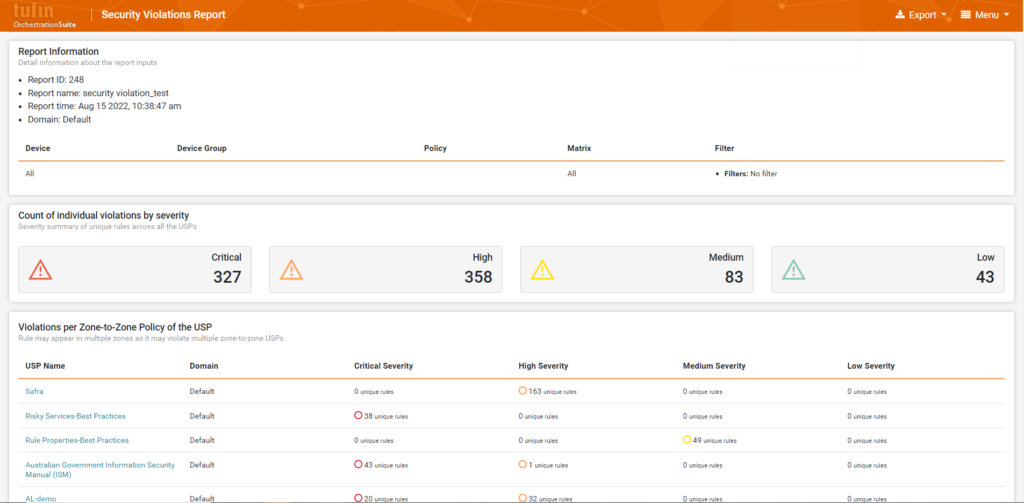
Compliance monitoring across thousands of network and cloud resources provides real-time risk awareness. Network teams can see risky access and firewall security policy violations in real-time from a central dashboard and receive alerts. The security policy monitoring solutions checks network changes against security/compliance policies, prioritizing violations by criticality.
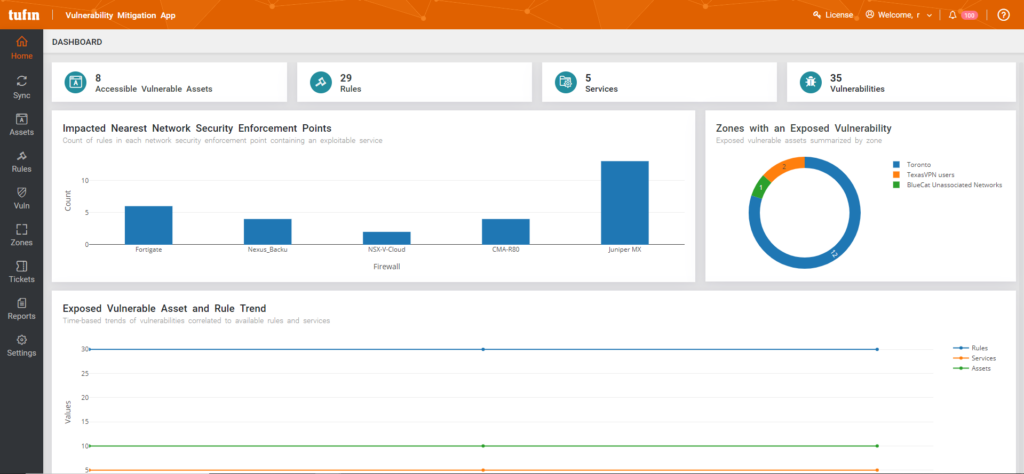
Tufin integrates with your vulnerability management solution, allowing you to correlate network topology intelligence with vulnerability scanning data. This allows you to prioritize patching faster.
Tufin supports several vulnerability scanning providers, including Rapid7, Tenable and more.
Tufin delivers the best network diagram and topology intelligence powers many of the capabilities that set Tufin apart from the competition. Centralize and automate network management on a single console with market leading accuracy and scalability.
Network maps visualize the entire network — IP addresses, subnets, cloud resources — and can identify issues such as excess network traffic or sudden downtime. This network performance monitoring allows IT teams and admins to quickly troubleshoot network issues for maximum security and minimal downtime.
Network visualization allows IT teams to quickly diagnose network issues, easily monitor devices like routers and servers, and plan for infrastructure that will require upgrading. Network visualization also enhances network control and security so network admins can understand new device interactions and identify suspicious nodes and links. This makes it easier to identify unknown devices and other threats across your on-premise and cloud-based environments.
Tufin’s network topology mapper and monitoring tool provides end-to-end network visibility others simply can’t match. It currently supports customers with 10,000+ network devices and more than 200 million routes.
As a network management solution, Tufin enables smooth change management and automates network security policy changes. Tools like SolarWinds Network Topology Mapper (NTM)offer similar key features, but lack the vendor-agnostic network security policy management and automation capabilities across firewalls and security groups that make Tufin such a standout tool.
Yes, Tufin provides seamless integrations with vendors that include Azure, AWS, Direct Connect, Express Route, Virtual WAN, Azure Load Balancers, AWS Gateway Load Balancers, and more.
Tufin is a compatible with the Linux operating system. As well as the Cloud-based platforms mentioned, Tufin provides seamless integrations with vendors such as Cisco, Palo Alto, Fortinet, Checkpoint and more, along with the ability to add new devices, providing detailed network diagrams which cover your entire network.
Elevate your network security and cloud security operations with Tufin's product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.