Leverage automated documentation of change management processes to ensure continuous compliance and minimize security issues, failed audits, and costly fines.
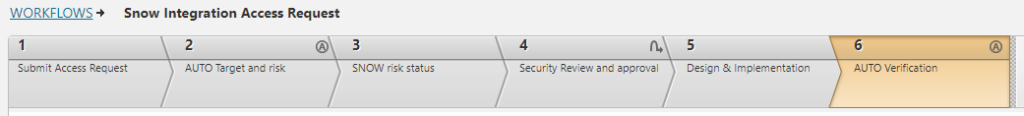
Demonstrate that actions have been quickly taken to meet compliance via on-demand, real-time reports.
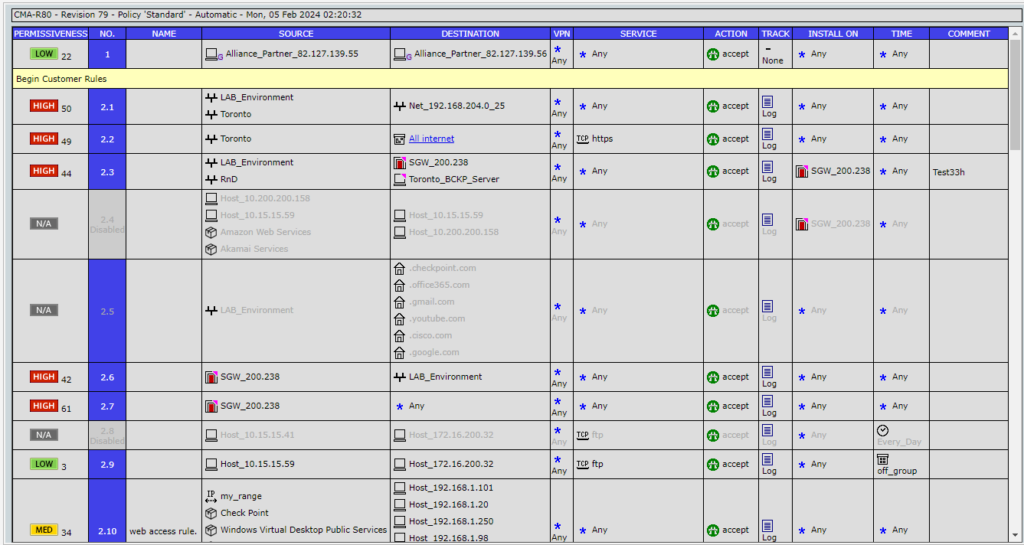
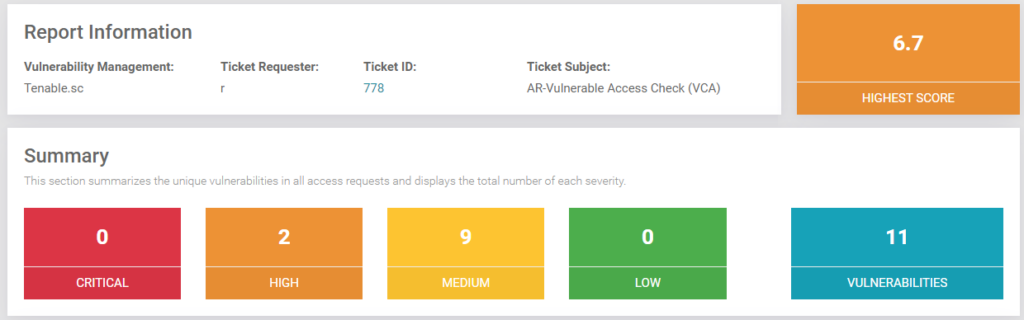
Reduce preparation time from weeks to days with automated processes and audit trails for all your firewalls, internal network devices, and cloud resources.
3 Ways to Get Started With Firewall Automation
9 Best Practices for Optimizing Firewall Performance
Demystifying Firewall Configuration: An Essential Guide
Firewall Change Management Best Practices: A Comprehensive Guide
Creating a Secure, Yet Manageable Firewall Policy for a Large Company – Firewall Expert Tip #10
Elevate your network security and cloud security operations with Tufin's product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.